February 1, 2023
Security Orchestration, the key to Vulnerability Management
Whether your IT department or security team needs to…
December 30, 2022
Reverse Engineering and Exploiting an IoT bug
In most of the write-ups of CTF, reverse engineering…
December 19, 2022
Prioritizing: making your Vulnerability Management Manageable
We orchestrate many scanners results at Faraday into the…
December 6, 2022
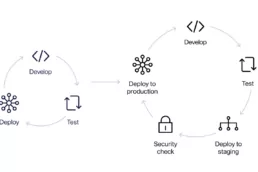
Faraday in the software development process – GitLab – Part 4
Pentesters use a comprehensive and complete toolkit to…
December 5, 2022
Faraday in the software development process – Jenkins – Part 2
We are going to integrate Jenkins into Faraday with…
November 30, 2022
Faraday in the software development process – Travis – Part 3
Pentesters use a comprehensive and complete toolkit to…
November 29, 2022
Faraday in the software development process – GitHub – Part 1
Pentesters use a comprehensive and complete toolkit to…