November 24, 2022
Pentesting toolkit: all you need to know
Pentesters use a comprehensive and complete toolkit to…
November 18, 2022
Exploring the Hidden Attack Surface of OEM IoT devices talk
The security of a company’s network also depends on the…
October 18, 2022
Bypassing passwords and getting a shell through UART in a Wi-Fi router
We started out by trying to connect to the router via UART…
October 5, 2022
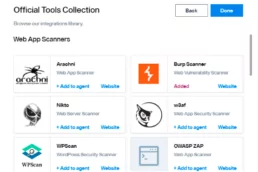
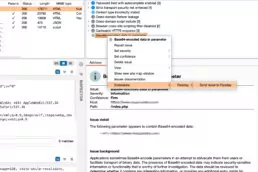
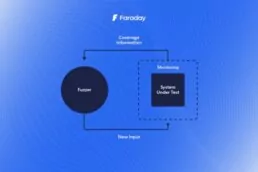
Automating Burp Suite with Faraday
Scaling security testing is hard if you are performing…
September 28, 2022
We updated Faraday Burp extender
We updated the Faraday Burp extender. Connect Burp to…
September 26, 2022
Our team’s vulnerabilities disclosures 2022
We devote time to reporting vulnerabilities in open-source…
September 22, 2022
Our team’s vulnerability disclosures 2021
Pentesters use a comprehensive and complete toolkit to…
September 8, 2022
A vulnerability in Realtek´s SDK for eCos OS: pwning thousands of routers
Pentesters use a comprehensive and complete toolkit to…