A vulnerability in Realtek´s SDK for eCos OS: pwning thousands of routers

When it comes to seeking vulnerabilities, we are professionals at it. It is in our DNA. We have a history of looking for vulns and there are certainly quite a few that we are very proud of.
This time, our team’s latest discovery went big and made it to DEFCON 30.
Now, we are presenting the details of this recently found vulnerability rated ‘high severity’: CVE 2022-27255
The curiosity and talent of our research team led to this major discovery; we couldn’t be happier for them.
Let’s dive into the details of their journey:
By 2023, the number of devices connected to IP networks will be more than three times the number of people worldwide. On the other hand, more people are working from home due to the pandemic. Because of this, the security of a company’s network also depends on the security of the home network of its employees. However, most consumer internet-connected devices have a reputation for being vulnerable. This was the starting point for our research team to seek and report security vulnerabilities in IoT devices, which led to the finding of an exploitable bug in a consumer-grade router popular in Argentina.
However, the impact of this vulnerability escalated quickly. Our researchers Octavio Gianatiempo (@ogianatiempo) and Octavio Galland (@GallandOctavio) presented it at DEFCON 30 in their talk “Exploring the hidden attack surface of OEM IoT devices: pwning thousands of routers with a vulnerability in Realtek’s SDK for eCos OS.”
“The vulnerability is a simple buffer overflow that can be triggered remotely without user interaction and under default settings. The vulnerable code is part of the networking stack; if the device is connected to the internet, an attacker only needs to send a packet to take control of the device,” said Octavio Gianatiempo when interviewed about the finding.


The vulnerable feature is called SIP ALG. This functionality rewrites SIP messages, a key part of VoIP communications, to ensure that devices on the local network can communicate with devices on the internet. SIP messages can contain SDP data that is used by the parties of the call to establish media sessions. When this implementation of SIP ALG tries to rewrite the media description field in the SDP data of a SIP message, it incurs in a stack buffer overflow by using strcpy without checking the destination buffer size. You can see the advisory here
The key part of this finding is that the vulnerability is present in multiple router models from different brands because this particular implementation of SIP ALG is part of a SDK from Realtek. “Realtek SDK for eCos is the code that Realtek provides to vendors who manufacture routers, access points, and repeaters powered by RTL819x family SoCs. This SDK implements the base functionalities of the router, for example, the web administration interface, the networking stack, etc. The vendors can build on top of this SDK to add custom functionalities and their branding to the device.”
“To identify affected products and vendors, our search process combines internet-wide scans, open-source intelligence, and automated firmware analysis. This process is still ongoing, and the number of affected vendors is closer to 20. However, more vendors might be affected that we haven’t found yet. Identifying affected OEM products is daunting due to the lack of visibility of their supply chain. For the moment, most of the identified devices are Tenda, Nexxt, and Intelbras. But there is also a D-Link router affected.” comments Gianatiempo.
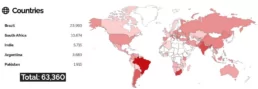
A preliminary Shodan search revealed over 60,000 vulnerable routers with their admin panel exposed worldwide. This admin panel is not enabled by default, so the total number of exposed devices should be greater. Remote identification of affected routers without this panel would require triggering the vulnerability, which is outside our research scope.
“Realtek informed customers about the eCos SDK vulnerability in March when it announced the availability of a patch. However, it’s up to the OEMs using the SDK to ensure that the patch is distributed to end-user devices,” writes Eduards Kovacs for SecurityWeek
Up to this date and to the best of our knowledge, no OEM or vendor has released a patched version of their firmware. And since many of these devices do not update automatically, when a patch becomes available, end users would still have to manually update their products. However, if vendors do not patch their firmwares, the best alternative should be to change to a different non-vulnerable product.
The bottom line of the finding is that, since vendors do not always plan long-term maintenance, security becomes an end user’s responsibility. This is why we are publishing the list of affected devices we have found so far alongside our detection tool to identify vulnerable firmware images. We encourage you to try it and help us find other vulnerable products.
Let’s help secure home networks as a community!
Here is the list of international newspapers where you can track the finding:
Related Posts
July 17, 2024
Using Faraday API for Vulnerability Management
Within our team, we prefer to focus on specific tasks depending on the type of host and the associated vulnerabilities. Exploiting a…
July 11, 2024
Our COO Martín Tartarelli talks about Vulnerabilities at UCEMA
Last week, our COO, Martin Tartarelli, offered a master class on vulnerabilities. He thoroughly explained what they are, how they work, and…
May 29, 2024
Good practices in Cybersecurity – Part 3
Good security practices go hand in hand with automation, integration, and collaboration. As dynamic as the threat landscape is, so must our…

