November 30, 2022
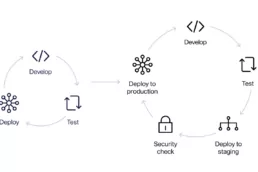
Faraday in the software development process – Travis – Part 3
Pentesters use a comprehensive and complete toolkit to…
November 29, 2022
Faraday in the software development process – GitHub – Part 1
Pentesters use a comprehensive and complete toolkit to…
November 24, 2022
Pentesting toolkit: all you need to know
Pentesters use a comprehensive and complete toolkit to…
November 18, 2022
Exploring the Hidden Attack Surface of OEM IoT devices talk
The security of a company’s network also depends on the…
November 9, 2022
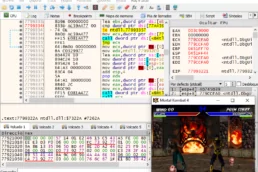
Reverse engineering and game hacking resources
If you are curious about reverse engineering, cybersecurity…
October 5, 2022
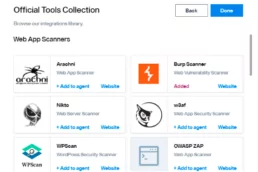
Automating Burp Suite with Faraday
Scaling security testing is hard if you are performing…
September 28, 2022
We updated Faraday Burp extender
We updated the Faraday Burp extender. Connect Burp to…
September 26, 2022
Our team’s vulnerabilities disclosures 2022
We devote time to reporting vulnerabilities in open-source…