October 18, 2022
Bypassing passwords and getting a shell through UART in a Wi-Fi router
We started out by trying to connect to the router via UART…
September 26, 2022
Our team’s vulnerabilities disclosures 2022
We devote time to reporting vulnerabilities in open-source…
September 8, 2022
A vulnerability in Realtek´s SDK for eCos OS: pwning thousands of routers
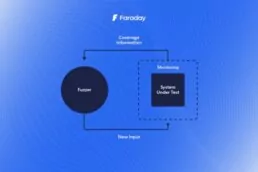
Pentesters use a comprehensive and complete toolkit to…
August 11, 2022
New research findings from Faraday goes to DEF CON
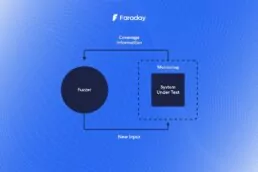
Pentesters use a comprehensive and complete toolkit to…
July 19, 2022
Securing open source software (Part 2)
Open-source software increases its presence in data…
July 17, 2022
Pentesting toolkit: all you need to know
Pentesters use a comprehensive and complete toolkit to…