March 11, 2025
Advisory: Multiple vulnerabilities affecting Draytek routers
Routers are critical to modern networks, acting as the…
February 25, 2025
Car Hacking with Doggie at H2HC!
Last month, Doggie took the stage at the Car Hacking…
November 27, 2023
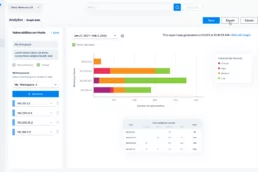
Visualize findings and understand your security posture
Our risk scoring system goes beyond mere criticality…
October 26, 2023
Faraday goes to Mind The Sec in São Pablo
Our Ssr. Researcher, Octavio Gianatiempo, presented his…
July 26, 2023
Federico Kirschbaum on a life in the Argentina hacking scene
“Hacking is a way of doing things, fixing problems, and…
June 7, 2023
Bugs and working from home, an interview with Federico Kirschbaum
The research states that the team was "seeking and…
February 1, 2023
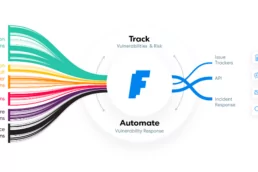
Security Orchestration, the key to Vulnerability Management
Whether your IT department or security team needs to…