We orchestrate many scanners results at Faraday into the same pipeline. This is how the process starts, but then we devote some time to deciding the importance or urgency of a vulnerability for our company. For this task, you need context information to reduce hundreds of critical vuln into a few and have more time to center your attention on what matters.Vulnerability management is an ever-changing field, with new threats and new solutions popping up all the time. The challenge is choosing the right way to handle vulnerabilities without getting buried in complexity. This blog post will walk you through some simple principles for prioritizing your vulnerability management process, so it doesn’t grow out of control. By the end, you should have a good idea of where to start if you’re looking to simplify your process while still coping with critical risks like remote code execution or database injection attacks.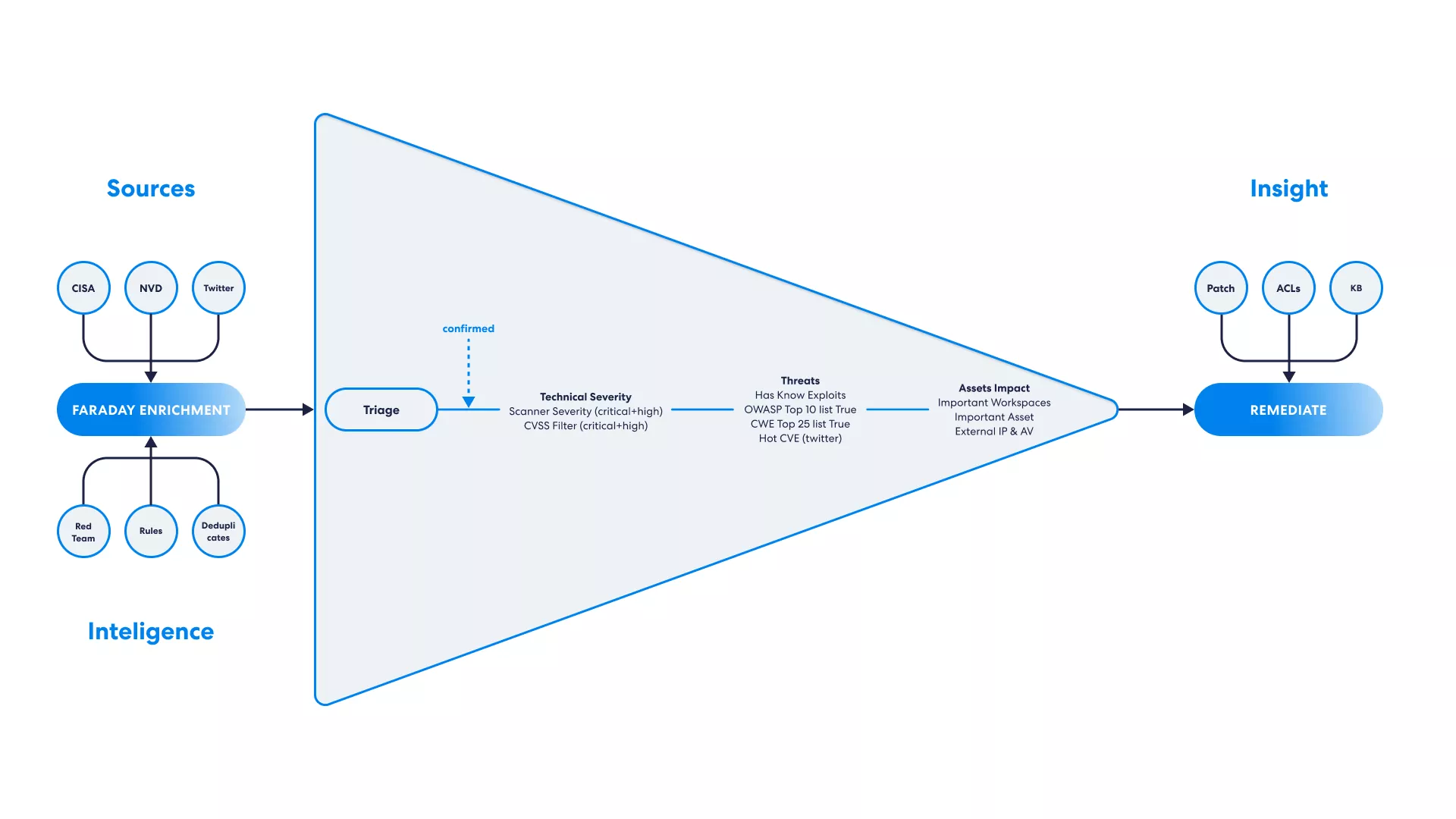 Any long-term vulnerability management process should have three key characteristics: First, it should be strategic — meaning it should have the security team’s resources in mind. If you’re not prioritizing smartly, you risk spending too much time on minor issues and not enough on the ones that matter most. Second, it should be repeatable — meaning you should be able to repeat the process again and again with consistent results. No organization can afford to wing it when managing vulnerabilities, especially in today’s hyper-connected digital world. Third, it should be efficient — meaning that taming the avalanche of findings should take less time. If it takes you more time to discover and report issues than it does to prevent them, you’re just spinning your wheels. A proactive approach is superior to a reactive one.
Any long-term vulnerability management process should have three key characteristics: First, it should be strategic — meaning it should have the security team’s resources in mind. If you’re not prioritizing smartly, you risk spending too much time on minor issues and not enough on the ones that matter most. Second, it should be repeatable — meaning you should be able to repeat the process again and again with consistent results. No organization can afford to wing it when managing vulnerabilities, especially in today’s hyper-connected digital world. Third, it should be efficient — meaning that taming the avalanche of findings should take less time. If it takes you more time to discover and report issues than it does to prevent them, you’re just spinning your wheels. A proactive approach is superior to a reactive one.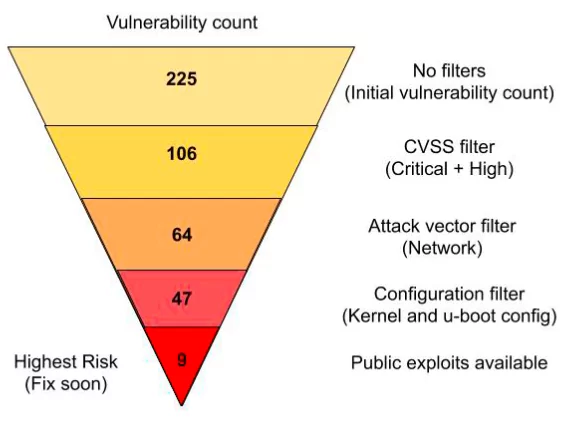
Which vulnerabilities should you focus on first? This is the most common question when we start working with new clients. Everyone wants to know which vulnerabilities are critical and worth focusing on. It’s a valid question, but it can also be misleading. Most companies have a list of thousands of vulnerabilities they need to fix because the CVSS treats all assets equally. So they try to prioritize that list based on the risk the vulnerability poses to their organization. Without considering those two additional factors – asset value and weaponization – you might prioritize patching vulnerabilities that aren’t likely to be exploited and leaving others that could expose even more sensitive assets if left unpatched. Your job is to identify each asset in terms of its risk and critical value
The urgency of a vulnerability is not always directly proportional to its risk. For example, noisy, frequent, and non-urgent vulns can be categorized as high but hardly exploitable. So if you want to prioritize your vulnerabilities based on urgency, you need to know your risk for each and give context. Our risk score is calculated based on the likelihood of a vulnerability exploitable. You can use this information to make an informed decision, prioritize your vulnerabilities and deal with your work mindfully and on your own terms. The vulnerabilities that have the highest likelihood and the highest impact should be your top priority.
So, where do we start?
1-Find vulnerabilities
2-Prioritize them by using our risk score and find out what you want to remediate first, and
3-Automatically delegate findings to teams who can best fix them.
This is how you’ll be able to focus your efforts on the vulnerabilities and services that pose the highest risk to your organization and be able to separate signal from noise.
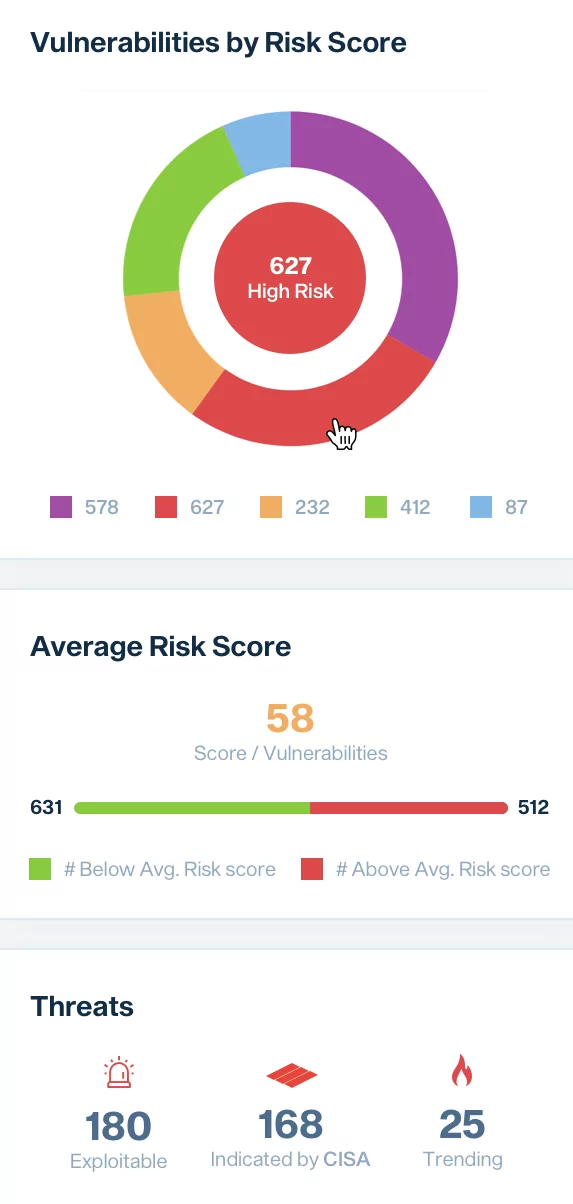
Concluding Thoughts
It can be tempting to try to fix everything at once. After all, that’s what most organizations hope to do. That’s why prioritizing vulnerabilities that are exploitable is so important. You can make the most of your time and resources by focusing on what truly matters. You can get ahead of the curve rather than playing catch-up, and you can build a stronger, more resilient organization that can better withstand attacks and breaches in the future.
At Faraday we help you detect exploitable vulnerabilities. We built a unique feature to select easily exploitable vulnerabilities that could most expose or hurt your infrastructure. Risk score: prioritize efficiently.Now all you have to do is check your vulnerability dashboard and see how the risk score works for each of the vulnerabilities: the higher the score, the more exploitable the vuln.If you have any questions, please book a meeting with our team





