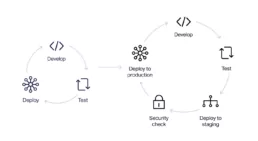
Faraday in the software development process – GitLab – Part 4
PentestingVulnerability ManagementWhitepaper
December 6, 2022
Pentesters use a comprehensive and complete toolkit to expose different platforms and evaluate the security of an IT infrastructure. They safely try to exploit vulnerabilities and are experts at reporting failures, data leakage, or other vulnerabilities.
Faraday in the software development process – Jenkins – Part 2
PentestingVulnerability ManagementWhitepaper
December 5, 2022
We are going to integrate Jenkins into Faraday with pipelines since this is one of the most extended CD/CI tools in the community. DevSecOps
Faraday in the software development process – GitHub – Part 1
PentestingVulnerability ManagementWhitepaper
November 29, 2022
Pentesters use a comprehensive and complete toolkit to expose different platforms and evaluate the security of an IT infrastructure. They safely try to exploit vulnerabilities and are experts at reporting failures, data leakage, or other vulnerabilities.
In this post, we present these tools and the several ways they can be applied.
Top 5 security tips: AWS Cloud Infrastructure
July 28, 2022
Improve your security posture on AWS Read the following recommendations and tips below to avoid these common cloud security issues. Top 5
Securing open source software (Part 2)
Open SourcePentestingCybersecWhitepaper
July 19, 2022
Open-source software increases its presence in data centers, consumer devices, and applications; also, its community continues to grow. Despite the code being available, memory safety issues persist in popular software. Our research team started a new quest to find and report vulnerabilities in the open-source projects we use every day. This is the second part of that job, where they share with us the strategy they used to find these bugs: coverage guided fuzzing.