Tips Nmap Script Engine

Nmap
Network Mapper is a popular network scanner that allows discovering ports and services, providing relevant information about a network. In addition to basic port scanning, Nmap offers a wide range of options and advanced functionalities. It can perform TCP, UDP, and SCTP scans, operating system detection scans, service version detection, script scans, and much more. It also allows customization of scans and generation of detailed reports.
Installation
Nmap is usually pre-installed in most Linux distributions. In case you don’t have it, you can easily install it with the following command:
apt-get install nmap
Scan Port Oneliner
If you want to quickly and simply test this tool, here is an example that you could use as a starting point:
nmap -sS -Pn -p 1-65535 -T4 -A <target>This command uses the following options:
-sS: Performs a SYN scan to determine which ports are open on the target.
-Pn: Skips host discovery and assumes the target is online.
-p 1-65535: Scans all possible ports on the target.
-T4: Sets the timeout value to 4, indicating a moderate scanning speed.
-A: Performs a detailed scan that includes operating system detection, software version detection, and script detection
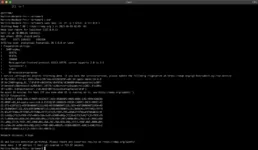
Nmap as Vulnerability Scanner
NSE (Nmap Scripting Engine) is a powerful scripting engine that allows for automation and extensibility of Nmap’s capabilities. NSE enables users to write and execute custom scripts to perform specific tasks during network scanning.
NSE is designed to interact with Nmap scan results and perform additional actions such as obtaining extra information about discovered services and systems, conducting security tests, detecting known vulnerabilities, and executing various scripting actions.
Some key features of NSE include:
– Predefined scripts: Nmap comes with an extensive collection of predefined scripts that can be used to perform common tasks such as service detection, system enumeration, searching for known vulnerabilities, etc.
– Custom script development: Users can write their own scripts using the Lua programming language. This allows for tailoring Nmap to specific needs and expanding its capabilities.
– Specialized scans: NSE can perform specialized scans that go beyond simple detection of open ports. For example, HTTP scans can be performed to search for insecure configurations, or SSL/TLS scans can be conducted to verify encryption settings.
– Integration with other systems: NSE scripts can also be integrated with other tools and systems, such as vulnerability databases or Security Information and Event Management (SIEM) systems, to facilitate data correlation and improve incident response.
Nmap – vuln
NSE scripts are categorized based on a set of predefined categories to which each script belongs, such as Authentication, Discovery, Brute Force, Malware, Version, and Vuln, just to name a few. You can find more detailed information about the different script categories in the following link.
The scripts categorized under vuln are intended to search for known vulnerabilities and report if they are identified on the target destination.
nmap -sV --script vuln <target>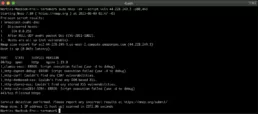
Nmap – vulners
Nmap-vulners is one of the most popular NSE scripts that utilizes the Vulners vulnerability database to search for and detect potential vulnerabilities in services and systems found during a network scan with Nmap.
The main difference between nmap-vulnand nmap-vulners lies in the vulnerability database used. Nmap-vuln uses its own internal database that is periodically updated with new vulnerability rules and signatures. On the other hand, nmap-vulners uses the Vulners database, which is regularly updated and is known for its extensive coverage of vulnerabilities. Vulners collects information from various sources, including vulnerability databases, security bulletins, public reports, etc.
To install it, you simply need to clone the repository into the scripts directory used by Nmap:
cd /usr/share/nmap/scripts/git clone https://github.com/vulnersCom/nmap-vulners.git
To execute it is very simple, you just need to pass the –-scriptargument to our Nmap command to indicate which NSE script to use:
nmap -sV --script vulners [--script-args mincvss=<arg_val>] <target>In case you want to scan a specific port, simply add the -p option at the end of the command, indicating the port number to scan:
nmap -sV --script nmap-vulners/ <target> -p80,443
TOP 10 NSE
Nmap has a large number of scripts, currently over 600. These scripts are designed to automate specific port scanning tasks and security analysis on systems and networks. Most of these scripts are pre-installed in Nmap and can be executed using the –script or -sC option. As mentioned in this post, additional scripts can also be downloaded from the official Nmap website or the Nmap Scripting Engine (NSE) community.
To let you test it out, we share a list of the top 10 Nmap scripts, in my opinion, that can be useful in a variety of situations:
http-title: This script retrieves the title of the web page and can help identify which application or service is hosted on the server.
– ssl-cert: This script displays information about the server’s SSL/TLS certificate and can help determine its validity.
– dns-brute: This script performs a brute force attack on the DNS server to obtain information about DNS records.
– ftp-anon: This script attempts to access the FTP server as an anonymous user to see if connection without credentials is allowed.
– smb-os-discovery: This script shows information about the operating system running on the SMB server.
– smtp-enum-users: This script performs a user enumeration attack on the SMTP server to discover valid usernames.
– snmp-brute: This script performs a brute force attack on the SNMP server to obtain information about the device.
– ssh-auth-methods: This script displays the authentication methods that are allowed on the SSH server.
– vuln: This script identifies known vulnerabilities on the server.
– whois-domain: This script retrieves information about the owner of a domain name.
Centralize and manage your vulnerabilities with Faraday.
If you want to centralize and integrate your security scans with Faraday, take a look at this documentation that shows you how to easily execute Nmap commands and import them into our platform.
Please note that to integrate Nmap with Faraday, you’ll need to follow these steps:
– Install Nmap: Make sure you have Nmap installed on your system. You can download and install it from the official Nmap website (https://nmap.org/).
– Install Faraday: Download and install Faraday on your system. You can obtain it from the official Faraday website (http://faradaysec.com/).
– Configure Faraday: Open Faraday and configure a client instance to connect to the Faraday server. This will allow you to manage the Nmap scan results from the Faraday interface.
– Configure Nmap to send results to Faraday: Open a terminal and execute the following command to generate an XML file with the Nmap scan results: nmap -oX scan_results.xml <opciones de escaneo> <target>
Make sure to replace <scan options> with the specific scanning options you want to use, and <target> with the IP address or IP range you want to scan.
– Import the results into Faraday: Once you have generated the XML file with the Nmap scan results, you can import it into Faraday using faraday-cli or the GUI.
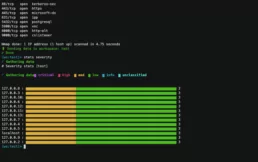
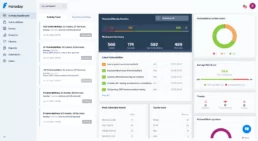
Your first scans integrated with Faraday.
Here are some snippets of different workflows you can generate using faraday-cli:
One-line Continuous Scan: Scan assets from a workspace.
$ faraday-cli host list -ip -w other_ws | nmap -iL - -oX /tmp/nmap.xml && faraday-cli tool report -w other_ws /tmp/nmap.xmlOne-Line to nmap all the hosts in the workspace and import the results back to Faraday:
To scan all the host lists inside a workspace with nmap and import the results back to Faraday.
for ip in $(faraday-cli host list -ip); faraday-cli tool run "nmap -Pn -p443,80 -sV --script=+http-enum -vvv $ip"!!! info In this case, you should have a workspace named “other_ws” with hostnames in it.
Faraday will process the command or XML file and display the Nmap scan results in its interface. You will be able to see information about the services and ports found, as well as any detected vulnerabilities.
This integration allows you to centrally manage the results of Nmap scans and keep a record of the vulnerabilities found in Faraday. Additionally, Faraday provides additional vulnerability management and reporting features that can further facilitate security analysis.
Remember to read the Faraday documentation for more detailed information on how to integrate Nmap with Faraday and make the most of their combined capabilities.
Related Posts
June 17, 2025
¿Tu empresa esta preparada para la nueva ley de ciberseguridad de Chile?
Desde este año entró en vigencia una ley modelo de ciberseguridad en Chile. La tomamos como referencia para desarrollar medidas clave que…
June 10, 2025
Release v5.14
Welcome to an enhanced version of the Faraday Vulnerability Management Platform. This is a quick but juicy release note where we are proud…
May 27, 2025
Automation and Pentesting: Use AI and Open-Source Tools
This article aims to combine automation and pentesting methodologies in a practical way, using artificial intelligence and multiple…


