What is Spring?
Spring is known to be an open source framework mainly used for the creation of Java applications. It’s actually much more than that, since its architecture and design are focused on efficiency and simplicity, but explaining more about this particular framework is not the purpose of this article. More information can be found here or here and its code is listed here.
How used is it?
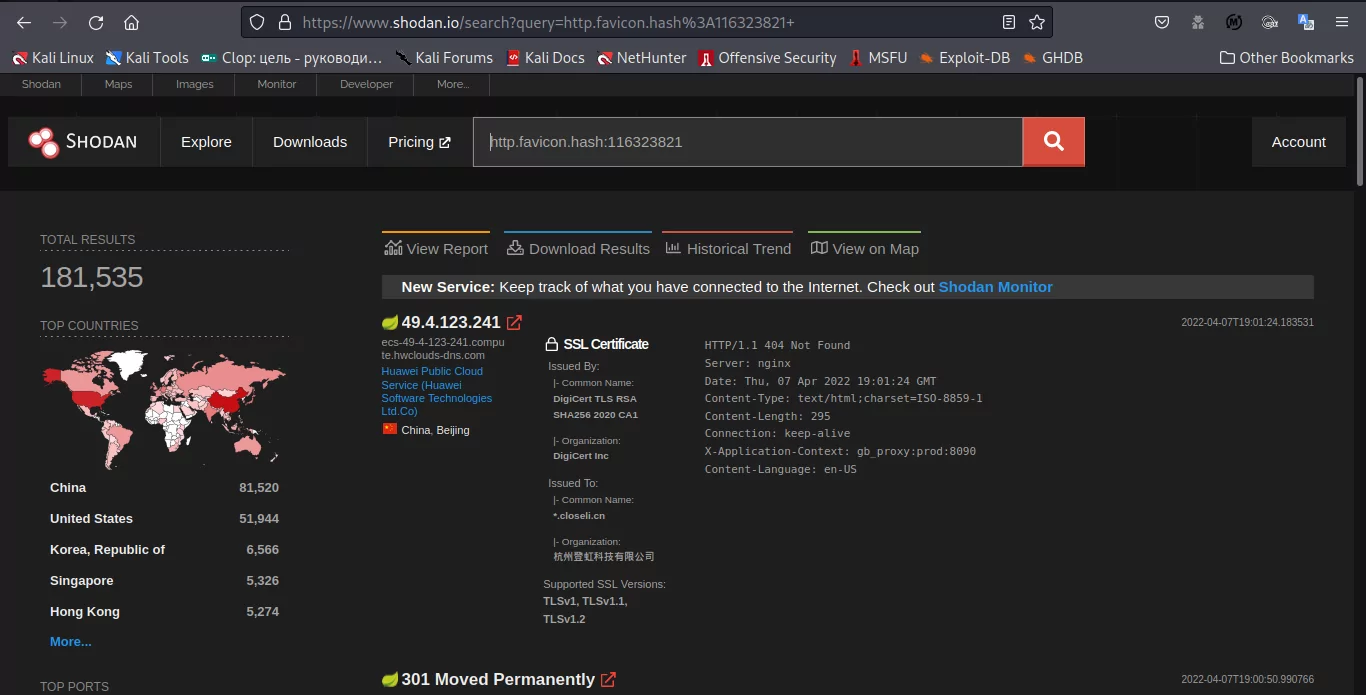
It’s possible to determine approximately how many internet-exposed servers have some version of Spring installed. For this, one of the options is shodan.
The technique utilized is basically a favicon hashing. The particular query in Shodan is “http.favicon.hash:116323821”.
In the following image we can see there are more than 180.000 active applications running some version of Spring:
Knowing a product’s hash’s favicon is fundamental. A code like the following one is used:
import mmh3
import requests
import codecs
headers = {
‘User-Agent’: ‘Mozilla’,
}
dir=input(‘link to favicon’)
response = requests.get(dir,headers=headers,verify=False)
favicon =codecs.encode(response.content,’base64′)
hash = mmh3.hash(favicon)
print (hash)
Spring4shell vulnerability
What is Spring4shell?
Spring4shell is a critical vulnerability (9.8/100) in Spring Core. It allows an attacker with no authentication privileges to execute a remote code. Particularly, this vulnerability affects Spring MVC and Spring WebFlux.
There are some requirements in order for an application to be vulnerable:
- JDK version >= 9.
- Spring should be installed in versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19 or previous ones.
- The application should be configured with Apache Tomcat as Servlets container.
- Spring-webmvc or spring-webflux dependencies.
- A WAR file format instead of a traditional JAR one.
Apart from being a critical vulnerability that affects many servers and applications, it was published before the security patch was released and a CVE had been assigned.
Nowadays, there are many Github repositories and pages with functional POCs:
https://github.com/BobTheShoplifter/Spring4Shell-POC
https://github.com/reznok/Spring4Shell-POC
https://github.com/WeiJiLab/Spring4Shell-POC
https://github.com/ckkok/spring4shell-poc
On the other hand, an “early announcement” was published at the Spring website a few days ago, mentioning the problem and informing about some patch releases and ways of fixing this vulnerability without having to change the version.
How to detect it? Am I vulnerable?
If the requirements for this application to be vulnerable are met, then it’s very likely that the vulnerability exists. However, hours after the first POC was published, there already were ways to make sure if the vulnerability existed:
- The ProjectDiscovery team launched a template for Nuclei (here).
- There are some repositories not officially linked to the Nmap project that contain scripts to detect it using the tool (here).
Are you interested in our products? Learn more🌟