June 5, 2023
Bypassing certificate pinning with Gabriel Franco
Many apps implement a security feature called Certificate…
June 1, 2023
Our co-founder Francisco Amato in Sepa’s night
Our CRO Francisco Amato was part of Sepa's Night. Watch the…
June 1, 2023
Our CEO Federico Kirschbaum at Buenos Aires City Legislature
After a cyber-attack on Buenos Aires City Legislature's…
December 19, 2022
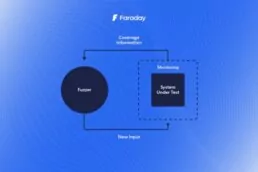
Prioritizing: making your Vulnerability Management Manageable
We orchestrate many scanners results at Faraday into the…
November 18, 2022
Exploring the Hidden Attack Surface of OEM IoT devices talk
The security of a company’s network also depends on the…
November 9, 2022
Reverse engineering and game hacking resources
If you are curious about reverse engineering, cybersecurity…
November 8, 2022
Our CEO Federico Kirschbaum at Argentina Fintech Forum
“Security is a culture; you set it up, learn from it, and…
September 26, 2022
Our team’s vulnerabilities disclosures 2022
We devote time to reporting vulnerabilities in open-source…
August 1, 2022
Cybersecurity is a secondary objective
A rapidly growing business must choose where to locate its…