DevSecOps: a thread

Let’s talk about security into the software development lifecycle. DevSecOps help you identify and mitigate security risks early in the development process, reducing the chance of a breach and improving the overall security of their apps.
This means designing security into the development process from the start. Here are some best practices for implementing DevSecOps in your organization:
1) Shift left: Incorporate security early in the development process by integrating security testing, security-focused code review process and analysis tools into the continuous integration and continuous delivery (CI/CD) pipeline. Security from design to deployment.
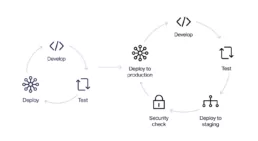
2) Implement automated security testing: Use automated tools to continuously scan the code and infrastructure for vulns, including static application security testing (SAST), dynamic application security testing (DAST), and interactive application security testing (IAST)
3)Use secure coding practices: Follow secure coding guidelines, such as OWASP Security guides. They are greatly helpful fOR DevSecOps.
4) Least privilege Principle: Use this approach to limit the access that users and systems have to sensitive resources and data. This reduces the potential damage that can be caused by an attacker or malicious software.
5) Awareness: Train developers and other team members on secure coding practices, and keep them up-to-date on the latest security threats and vulnerabilities. Foster the culture and collaboration between development and security teams.

6) Continuous security and update: Monitor the software in production to identify and address any security issues. Also, keep the software up-to-date with security patches and updates.

Related Posts
October 7, 2024
Maturity Models in Vulnerability Management: Where Are You At?
Since organizations differ in size, structure, and maturity, there are various vulnerability management models tailored to each. These…
July 29, 2024
Expanded Attack Surface: How to Optimize Time and Resources in Cybersecurity
Security teams of all sizes, from large Fortune 500 companies to small NGOs, face the same problem: a lack of time and an ever-expanding…
July 17, 2024
Using Faraday API for Vulnerability Management
Within our team, we prefer to focus on specific tasks depending on the type of host and the associated vulnerabilities. Exploiting a…


