Whether your IT department or security team needs to operate and protect your system and data, vulnerability management tools are the way to go. They offer the best way to coordinate and automate the process from beginning to end. It is called Orchestration. It is one of the key concepts to bear in mind when doing vuln management.
All in one single platform
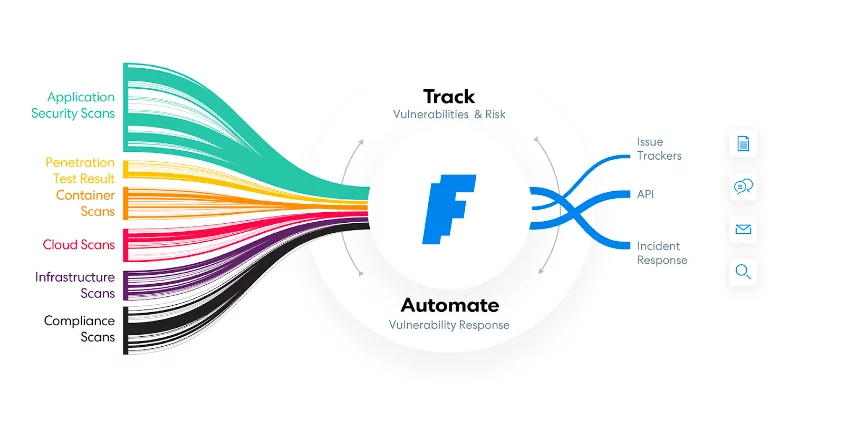
Orchestration in cybersecurity refers to the process of organizing and automating the execution of security-related tasks and workflows across multiple devices, systems, and platforms. It is one of the most efficient ways to connect security systems and integrate multiple security tools, improving incident response times, threat detection, and compliance.
The goal of orchestration is to streamline and optimize the management of security operations and bring together several tools—both security and non-security—by merging them. For example, teams may deploy and automate their custom set of scanners, monitor and prioritize their vulnerabilities, generate reports of their findings, and send tickets to Jira or ServiceNow, all with an intuitive interface that allows them to save time by automating repetitive tasks.
Faraday is a platform that orchestrates security tools in a way that optimizes response time and efficiency for vulnerability management. We allow security teams to automate repetitive tasks and coordinate their efforts by working collaboratively across different teams and systems. Plus, we work with more than 100 scanners.
How to cope with security when you are a team of one
 By automating the vulnerability scanning process across all systems in the network and then prioritizing the vulnerabilities based on their risk level, orchestration can help security experts more effectively manage the large volume of vulnerabilities present in modern IT environments. Additionally, orchestration provides clear and easy-to-do reports and alerts to the security team to take action on vulnerabilities that are not patched yet.
By automating the vulnerability scanning process across all systems in the network and then prioritizing the vulnerabilities based on their risk level, orchestration can help security experts more effectively manage the large volume of vulnerabilities present in modern IT environments. Additionally, orchestration provides clear and easy-to-do reports and alerts to the security team to take action on vulnerabilities that are not patched yet.
Depending on the size of your infrastructure, when you use a vuln management collaborative orchestration tool, you can reduce time spent sitting at a PC.
The platform takes care of everything in one place, from automating scans to reporting.
This is a great point for us to jump off a problem that brings a lot of concern in the industry: the shortage of cybersecurity expertise and, at the same time, the rise of ransomware and all kinds of aggression to your infrastructure and data.
Security platforms that orchestrate can and were built to take care of these difficulties:
They are security packages that will allow you to track, filter and confirm all your findings, generate reports all in one place.
Moreover, it can be run by any systems administrator and become part of their daily responsibilities. This is a user-friendly platform designed to make the team’s lives easier.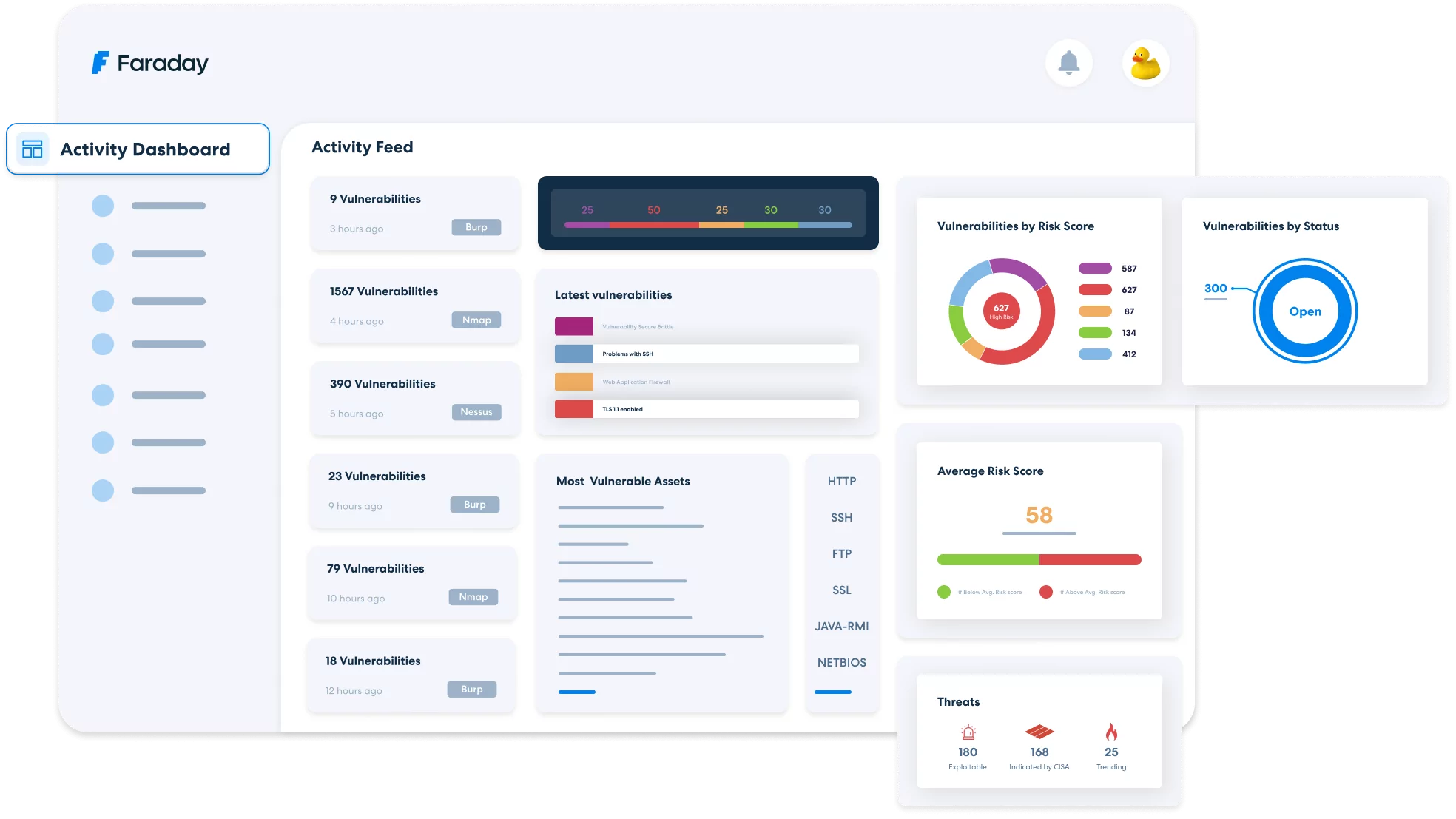
Key components of orchestration
Let’s go behind the scenes of orchestration. These are the key components:
Automation: Automating repetitive tasks and workflows, such as vulnerability scanning and patch management, can help to streamline security operations and improve efficiency.
Coordination: Coordinating the efforts of different teams and systems can ensure that security operations are aligned with the organization’s overall goals and objectives.
Prioritization: Prioritizing tasks and vulnerabilities based on their risk level can help to ensure that the most critical issues are addressed first.
Reporting and Alerting: Providing real-time reports and alerts on security incidents and vulnerabilities can help security teams to identify and respond to potential threats quickly.
Incident Response: Automating incident response and investigations can help security teams quickly and effectively respond to security incidents.
Compliance: Ensuring compliance with relevant regulations and standards can help to minimize the risk of regulatory fines and reputational damage.
Integration: Integrating with other security tools and systems can help improve security operations’ overall effectiveness.
Auditing: Auditing the overall orchestration process and its effectiveness helps identify gaps and improve the overall security posture.
Orchestration looks pretty much like choreography in which each element adds up to the final result. It all happens harmoniously and smoothly. Just like in here:Orchestration aims at taking care of everything in one place, from reporting to scanning. At Faraday, we built a pipeline that collects data from various sources to offer in-depth insights into the threat environment. The results from multiple scans are compiled into one dashboard, making remediation processes more effective.