This research project started when Javier’s wife, our ex Research leader, told him their IP camera had stopped working. Javier was asked to fix it, but, as a security researcher, the temptation was too great. He brought the camera to the office and discussed the problem with Octavio, another security researcher at Faraday. The situation quickly escalated from some light reverse engineering to a full-fledged vulnerability research project, which ended with two high-severity bugs and an exploitation strategy worthy of the big screen.
Octavio and Javier uncovered two LAN remote code execution vulnerabilities in EZVIZ’s implementation of Hikvision’s Search Active Devices Protocol (SADP) and SDK server:
– CVE-2023-34551: EZVIZ’s implementation of Hikvision’s SDK server post-auth stack buffer overflows (CVSS3 8.0 – HIGH)
– CVE-2023-34552: EZVIZ’s implementation of Hikvision’s SADP packet parser pre-auth stack buffer overflows (CVSS3 8.8 – HIGH)
The affected code is present in several EZVIZ products, which include but are not limited to: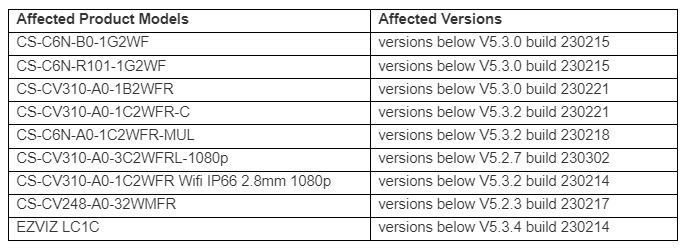 These vulnerabilities affect IP cameras and can be used to execute code remotely, so they drew inspiration from the movies and decided to recreate an attack often seen in heist films. The hacker in the group is responsible for hijacking the cameras and modifying the feed to avoid detection. Take, for example, this famous scene from Ocean’s Eleven:Exploiting either of these vulnerabilities, Javier and Octavio served a victim an arbitrary video stream by tunneling their connection with the camera into an attacker-controlled server while leaving all other camera features operational. If you want to take a deep dive into the whole research process, you should check out the slides and code for the presentation and demo they showcased at DEFCON 31 Hardware Hacking Village and the recording of their talk at Ekoparty 2023. They cover firmware analysis, vulnerability discovery, building a toolchain to compile a debugger for the target, developing an exploit capable of bypassing ASLR, and all the details about the Hollywood-style post-exploitation, including tracing, in memory code patching and manipulating the execution of the binary that implements most of the camera features.This research shows that memory corruption vulnerabilities still abound on embedded and IoT devices, even on products marketed for security applications like IP cameras. Memory corruption vulnerabilities can be detected by static analysis, and implementing secure development practices can reduce their occurrence. These approaches are standard in other industries, evidencing that security is not a priority for embedded and IoT device manufacturers, even when developing security-related products. By filling the gap between IoT hacking and the big screen, this research questions the integrity of video surveillance systems and hopes to raise awareness about the security risks posed by these kinds of devices.Disclosure timeline2022-12-19: Initial contact with EZVIZ asking for a secure channel for disclosure.
These vulnerabilities affect IP cameras and can be used to execute code remotely, so they drew inspiration from the movies and decided to recreate an attack often seen in heist films. The hacker in the group is responsible for hijacking the cameras and modifying the feed to avoid detection. Take, for example, this famous scene from Ocean’s Eleven:Exploiting either of these vulnerabilities, Javier and Octavio served a victim an arbitrary video stream by tunneling their connection with the camera into an attacker-controlled server while leaving all other camera features operational. If you want to take a deep dive into the whole research process, you should check out the slides and code for the presentation and demo they showcased at DEFCON 31 Hardware Hacking Village and the recording of their talk at Ekoparty 2023. They cover firmware analysis, vulnerability discovery, building a toolchain to compile a debugger for the target, developing an exploit capable of bypassing ASLR, and all the details about the Hollywood-style post-exploitation, including tracing, in memory code patching and manipulating the execution of the binary that implements most of the camera features.This research shows that memory corruption vulnerabilities still abound on embedded and IoT devices, even on products marketed for security applications like IP cameras. Memory corruption vulnerabilities can be detected by static analysis, and implementing secure development practices can reduce their occurrence. These approaches are standard in other industries, evidencing that security is not a priority for embedded and IoT device manufacturers, even when developing security-related products. By filling the gap between IoT hacking and the big screen, this research questions the integrity of video surveillance systems and hopes to raise awareness about the security risks posed by these kinds of devices.Disclosure timeline2022-12-19: Initial contact with EZVIZ asking for a secure channel for disclosure.
2022-12-27: SADP buffer overflows report sent.
2023-01-14: The EZVIZ security team acknowledged the SADP vulnerability.
2023-01-19: SDK server buffer overflows report sent.
2023-02-07: The EZVIZ security team acknowledged the SDK vulnerability and shared their remediation plan and timeline.
2023-04-03: EZVIZ patched the affected firmware versions.
2023-06-16: CVE identifiers were assigned for the reported vulnerabilities.
2023-07-26: EZVIZ released a security advisory.
If you are interested in any of our products and services, please contact us.
