Good practices in Cybersecurity – Part 1

Good practices in cybersecurity, which have a long-lasting positive impact, need to be ingrained in daily routines and considered a fundamental part of your workflow.
Every journey has to start somewhere, and it starts here.
We are delighted to present the first article of our three-part series on Good Practices in Cybersecurity: a comprehensive guide designed to kick-start your journey with a detailed and useful checklist.
DevSecOps Security
The number of technologies one decides to implement becomes irrelevant; the weakest link in the chain will always be the human factor, and this should be the starting point for any DevSecOps implementation.
One of the most important aspects of DevSecOps involves challenging how traditional security teams integrate with the overall business. Changing habits and creating awareness at all levels of a company are not easy tasks and require a top-down approach if certain attitudes are to be modified.
Below are specific practices recommended for implementation:
Breaking down barriers with security champions
For effective security, security matters (and a security mindset) need to be included as early as possible in the software delivery pipeline. One way to do this is through security champions.
Security champions are members of a team who assist in making decisions about when and how to address security matters. They act as the security voice for a specific product or team, and also assist in prioritizing security bugs for their team or area.
Some of the most important tasks of a security champion include:
– Emphasizing security matters across all teams.
– Evangelizing a security mindset.
– Ensuring security is not blocking active developments or reviews.
– Empowered to make decisions.
– Working with the AppSec team on mitigation strategies.
– Collaborating with QA and Testing.
– Writing tests (from unit tests to integration tests).
– Assisting with the development of CI environments.
Training and improving team skills
Any successful DevSecOps program will invest in good training and professional development for its team.
Training should be rooted in the goals, policies, and standards for software security within the company, and learning methods should be flexible and tailored. To foster and develop a good security team, organizations should provide new hires with appropriate training and tools needed to perform their jobs correctly, contributing to the successful release of secure software.
Involving security and DevOps specialists, training organizations to enhance team skills and awareness, are essential to maintaining consumer trust. Good training ensures that standards are implemented correctly.
Culture is everything
Simply having the right DevSecOps procedures and technologies will not be enough to achieve anything if the company culture does not allow those processes and technology to be used properly.
Traditionally, the security team has been an obstacle to release performance. It has become the “Department of No,” and as a result, they are excluded over time, creating a self-reinforced spiral of division between teams. DevSecOps aims to break down these barriers and prevent security from disregarding the entire business when implementing policies or tools.
Once DevSecOps is fully embraced, there is no longer a “Security Team,” but rather a security mindset that constantly evolves throughout the company.
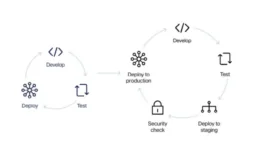
Process integration
Integrating information security into agile development enables organizations to have a completely secure workflow through each stage of the software development lifecycle.
In agile methodologies, security integration should begin at the earliest stage possible, which in most cases is the requirements definition stage. This methodology strives to reduce the cost of implementing security.
Version control, metadata, and orchestration
In an automated world, change is the only constant, and change needs to be both consistent and traceable. To track all changes, it must be ensured that there is adequate and immutable version control.
To enable quick recovery, each action needs a version so that it can be managed in the same way as source code. Once converted into metadata, team operations can track a change and apply metrics.
Software orchestration not only provides a repeatable methodology for deploying infrastructure but also provides a wealth of metadata related to any task. This metadata can not only be used by the software orchestration itself, but also as an authoritative source for integrated tools. Once coupled with version control, software orchestration becomes a powerful source of information for all operational teams.
Trainings, red teaming services, or continuous scanning? We’ve got you covered. Reach out for more information.
Related Posts
June 17, 2025
¿Tu empresa esta preparada para la nueva ley de ciberseguridad de Chile?
Desde este año entró en vigencia una ley modelo de ciberseguridad en Chile. La tomamos como referencia para desarrollar medidas clave que…
June 10, 2025
Release v5.14
Welcome to an enhanced version of the Faraday Vulnerability Management Platform. This is a quick but juicy release note where we are proud…
May 27, 2025
Automation and Pentesting: Use AI and Open-Source Tools
This article aims to combine automation and pentesting methodologies in a practical way, using artificial intelligence and multiple…


