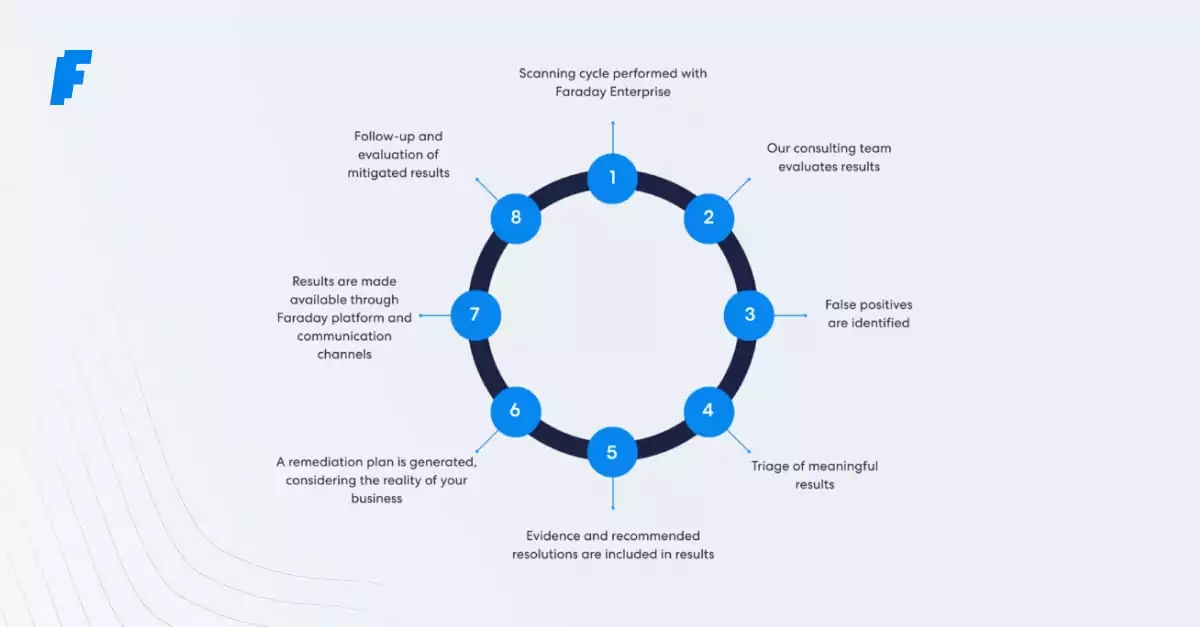
Hablemos de la seguridad en el ciclo de vida del desarrollo de software. DevSecOps hAyudarle a identificar y mitigar los riesgos de seguridadks en una fase temprana del proceso de desarrollo, lo que reduce la posibilidad de que se produzca una infracción y mejora la seguridad general de sus aplicaciones.
Esto significa integrar la seguridad en el proceso de desarrollo desde el principio. Estas son algunas de las mejores prácticas para implantar DevSecOps in su organización:
1) Desplazamiento a la izquierda: Incorpore la seguridad en una fase temprana del proceso de desarrollo integrando las pruebas de seguridad, el proceso de revisión del código centrado en la seguridad y las herramientas de análisis en el proceso de integración y entrega continuas (CI/CD). Seguridad desde el diseño hasta el despliegue.
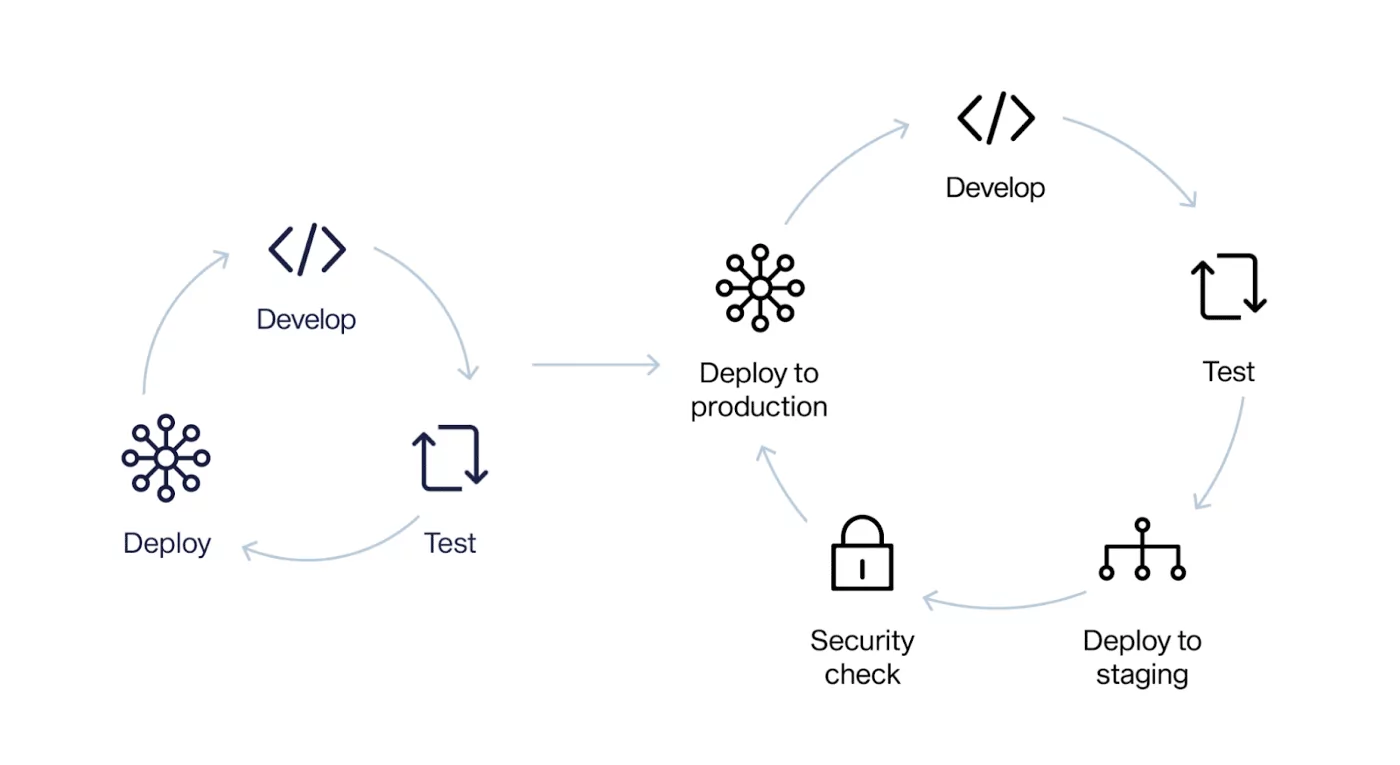 2) Implemente pruebas de seguridad automatizadas: Utilice herramientas automatizadas para escanear continuamente el código y la infraestructura en busca de vulnerabilidades, incluidas pruebas estáticas de seguridad de aplicaciones (SAST), pruebas dinámicas de seguridad de aplicaciones (DAST) y pruebas interactivas de seguridad de aplicaciones (IAST).
2) Implemente pruebas de seguridad automatizadas: Utilice herramientas automatizadas para escanear continuamente el código y la infraestructura en busca de vulnerabilidades, incluidas pruebas estáticas de seguridad de aplicaciones (SAST), pruebas dinámicas de seguridad de aplicaciones (DAST) y pruebas interactivas de seguridad de aplicaciones (IAST).
3)Utiliza prácticas de codificación seguras: Siga las directrices de codificación segura, como OWASP Security. Son de gran ayuda para DevSecOps.
4) Principio del mínimo privilegio: utilice este enfoque para limitar el acceso de usuarios y sistemas a recursos y datos sensibles. Esto reduce el daño potencial que puede causar un atacante o un software malicioso.
5) Concienciación: Forme a los desarrolladores y otros miembros del equipo en prácticas de codificación seguras, y manténgalos al día sobre las últimas amenazas y vulnerabilidades de seguridad. Fomente la cultura y la colaboración entre los equipos de desarrollo y seguridad. 6) Seguridad y actualización continuas: Supervise el software en producción para identificar y solucionar cualquier problema de seguridad. Además, mantén el software al día con parches de seguridad y actualizaciones.
6) Seguridad y actualización continuas: Supervise el software en producción para identificar y solucionar cualquier problema de seguridad. Además, mantén el software al día con parches de seguridad y actualizaciones.