
During red team assessments, our Research team found that personal information leaked in breaches can pose a significant risk to our clients. It is often the case that personal passwords are reused in enterprise environments. But even when they aren’t reused, these passwords, in conjunction with other personal information, can be used to derive working credentials for employer resources.
Collecting this information manually is a tedious process. Therefore, our Head of Research Javier Aguinaga and Head of Security Services Gabriel Franco developed a tool that helps them quickly identify any leaked employee information associated with their clients. The tool proved to be incredibly useful for their team when used internally. However, they recognized the potential benefits it could offer to other organizations facing similar security challenges. As a result, they made the decision to open-source the tool.
This security tool enables the collection of personal information through Open Source Intelligence techniques. It starts by taking a company domain and retrieving a list of employees from LinkedIn. Subsequently, it gathers data on individuals across various social media platforms, such as Twitter, LinkedIn, GitHub, GitLab, and more, with the goal of obtaining personal email addresses. Once these email addresses are found, the tool searches through the COMB database and other internet sources to check if the user’s password has been exposed in any breaches.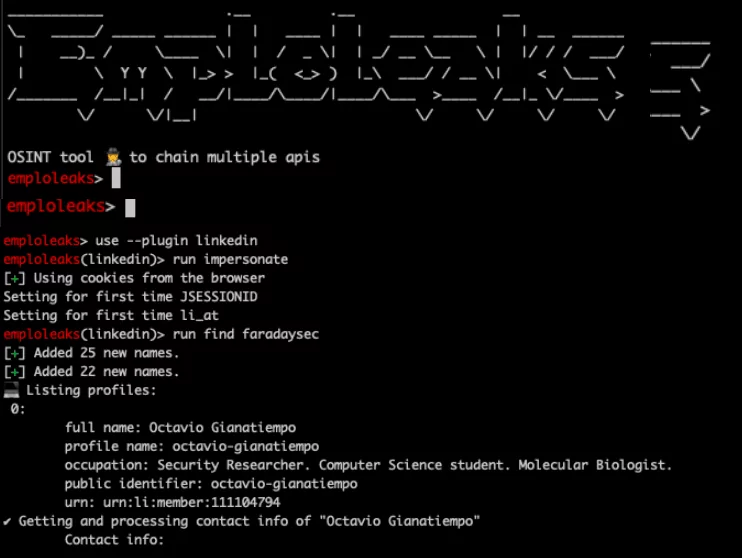 Password reuse is a common method attackers use to breach organizations. Companies need a straightforward way to understand their attack surface and help their employees comprehend their level of exposure. While our team know several tools that work independently, they decided to automate each phase, starting with a company name, then searching every employee and their social networks to obtain personal emails, and finally identifying potentially leaked passwords. They query various websites and indexed public breached databases to promptly obtain results.
Password reuse is a common method attackers use to breach organizations. Companies need a straightforward way to understand their attack surface and help their employees comprehend their level of exposure. While our team know several tools that work independently, they decided to automate each phase, starting with a company name, then searching every employee and their social networks to obtain personal emails, and finally identifying potentially leaked passwords. They query various websites and indexed public breached databases to promptly obtain results.
By making this tool openly available, our team can help organizations proactively identify and mitigate the risks associated with leaked employee credentials. This will ultimately contribute to a more secure digital ecosystem for everyone.
Check out the project on GitHub
Tool Details
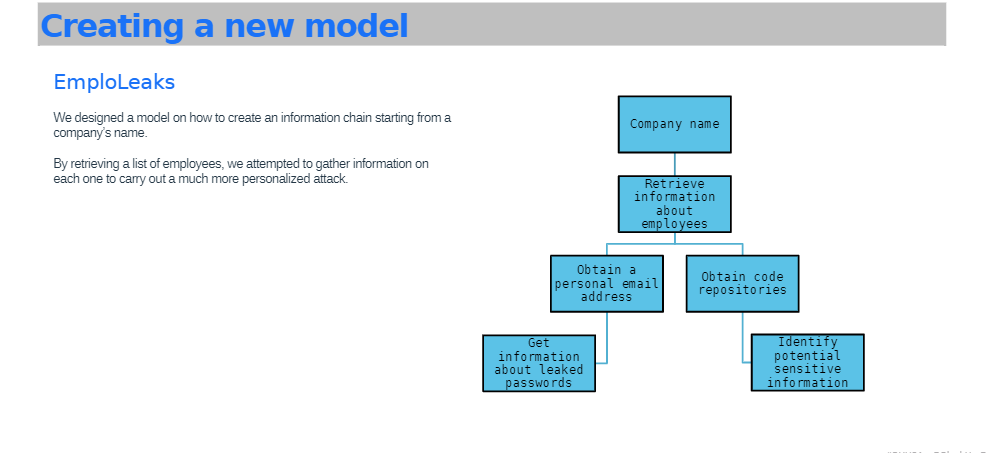 This security tool was built in Python and allows companies to easily gather information about their employees and assess their online exposure. By automating the data collection process, their tool saves time and effort, eliminating the need to manually search through various social media platforms and databases. This enables companies to identify potential security risks more efficiently and take preemptive measures to protect sensitive information.
This security tool was built in Python and allows companies to easily gather information about their employees and assess their online exposure. By automating the data collection process, their tool saves time and effort, eliminating the need to manually search through various social media platforms and databases. This enables companies to identify potential security risks more efficiently and take preemptive measures to protect sensitive information.
One of the key benefits of the tool is that it is completely free to use. This enables companies, particularly those with smaller budgets, to assess their security posture without incurring additional costs. It also provides a comprehensive report on online employee presence, highlighting any exposed passwords that may exist. This can help companies take proactive measures to address potential security risks before they escalate.
Our team’s current focus is on ensuring that the application flow is efficient, and they are diligently addressing any bugs that arise as soon as possible. This is an ongoing process, and they are committed to providing a high-quality tool that is reliable and meets the needs of the community. As they still are in a development phase, they welcome feedback and contributions from users to help them enhance the tool further.
Check out the project on GitHub
This tool was presented at Black Hat Arsenal 2023





