Continuous Security
Continuous Security
Protege tu superficie de ataque
Protege tu superficie de ataque
En un mundo ágil y dinámico, la seguridad necesita un enfoque dinámico y continuo. Se trata más de monitorear y evaluar de forma constante tu superficie de ataque aplicando técnicas y metodologías que usan los atacantes.
En un mundo ágil y dinámico, la seguridad necesita un enfoque dinámico y continuo. Se trata más de monitorear y evaluar de forma constante tu superficie de ataque aplicando técnicas y metodologías que usan los atacantes.
Habla con nuestros expertos
¿Por qué Continuous Security?
¿Por qué Continuous Security?
● Visibilidad en tiempo real: Ni antes. Ni después. Tené un seguimiento constante de tu superficie de ataque. Supervisa la seguridad de tu infraestructura.
● Priorización: Las empresas pueden tener más de 100.000 vulnerabilidades, pero el 85% no se puede explotar de manera realista. . Enfócate solo en las vulnerabilidades que pongan en riesgo tu infraestructura.
● Reportes accionables: Recibí datos actualizados y métricas claras para tomar las mejores decisiones.
● Visibilidad en tiempo real: Ni antes. Ni después. Tené un seguimiento constante de tu superficie de ataque. Supervisa la seguridad de tu infraestructura.
● Priorización: Las empresas pueden tener más de 100.000 vulnerabilidades, pero el 85% no se puede explotar de manera realista. . Enfócate solo en las vulnerabilidades que pongan en riesgo tu infraestructura.
● Reportes accionables: Recibí datos actualizados y métricas claras para tomar las mejores decisiones.
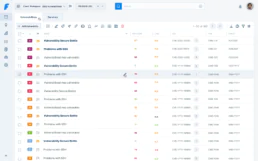
Nuestra plataforma de Gestión de Vulnerabilidades
Centraliza y optimiza el proceso de gestión de vulnerabilidades, haciéndolo más ágil y escalable. Clasifica, prioriza y maneja las vulnerabilidades de manera eficiente, mientras automatizas pasos clave del proceso.
Faraday Platform
Nuestra herramienta te permite definir y ejecutar acciones desde diferentes fuentes y a tu medida e importar automáticamente los resultados en tu repositorio. Con más de 150 integraciones, un Faraday-Cli fácil de usar, una API RESTful y un esquema flexible para desarrollar tus propios agentes, nuestra plataforma ofrece una alternativa única para manejar tus vulnerabilidades de forma automática y colaborativa.
Nuestra plataforma de Gestión de Vulnerabilidades Centraliza y optimiza el proceso de gestión de vulnerabilidades, haciéndolo más ágil y escalable. Clasifica, prioriza y maneja las vulnerabilidades de manera eficiente, mientras automatizas pasos clave del proceso.
Nuestra herramienta te permite definir y ejecutar acciones desde diferentes fuentes y a tu medida e importar automáticamente los resultados en tu repositorio. Con más de 150 integraciones, un Faraday-Cli fácil de usar, una API RESTful y un esquema flexible para desarrollar tus propios agentes, nuestra plataforma ofrece una alternativa única para manejar tus vulnerabilidades de forma automática y colaborativa.
Metodología de trabajo
Metodología de trabajo
Después de iniciar sesión
Después de iniciar sesión
Proceso de seguridad continua
Proceso de seguridad continua
Empower your reporting
Empower your reporting
There are two ways of finding vulnerabilities: either you do it, or someone else will.
How it works
How it works
Faraday was designed to ease every step of your job
Discover
Integrate, scan, and effectively utilize our robust tool for comprehensive network, application, and system scanning.
Document findings
Easily document and organize your findings, including vulnerability details, severity levels, and recommendations.
Generate reports
Generate comprehensive reports that provide a clear overview of discovered vulnerabilities and recommended actions.
Client Communication
Share reports with clients to facilitate effective communication and understanding of identified risks.
Secure your infrastructure with Faraday as your ally
Smart decisions come from automatized intelligent reporting. By identifying potential threats and providing actionable remediation recommendations to your colleagues and customers, you help protect organizations from cyber attacks.
Secure your infrastructure with Faraday as your ally
Smart decisions come from automatized intelligent reporting. By identifying potential threats and providing actionable remediation recommendations to your colleagues and customers, you help protect organizations from cyber attacks.
Comprehensive Pentesting
for your Business Security
Prevent data breaches
Meet compliance requirements
Build customer trust
Comprehensive Pentesting for your business security
Prevent data breaches
Meet compliance requirements
Build customer trust
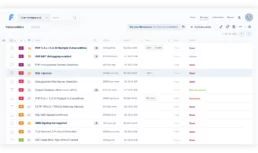
Simplify Your Assessments with Faraday
Simplify Your Assessments with Faraday
Managing multiple assessments can be overwhelming, but Faraday makes it easy. With centralized management, you can manage all your results and vulnerabilities in one place.
Third-Party integrations in order to save the best value: Your time
Integrating Faraday with other popular tools used in the pentesting process, such as Nmap, Metasploit, and Burp Suite, has never been easier. This integration makes it easy to import data from other tools into Faraday, saving you time and effort. With Faraday’s integration capabilities, you can work more efficiently and effectively.
Third-Party integrations in order to save the best value: Your time
Integrating Faraday with other popular tools used in the pentesting process, such as Nmap, Metasploit, and Burp Suite, has never been easier. This integration makes it easy to import data from other tools into Faraday, saving you time and effort. With Faraday’s integration capabilities, you can work more efficiently and effectively.
Showcase your Progresss
With Faraday, you can show your work in real-time, which provides transparency and instills trust with your clients. Automatically provide all types of evidence and information, such as vulnerability severity, recommended remediation steps, and proof-of-concept code. Take your assessments to the next level.
Showcase your Progresss
With Faraday, you can show your work in real-time, which provides transparency and instills trust with your clients. Automatically provide all types of evidence and information, such as vulnerability severity, recommended remediation steps, and proof-of-concept code. Take your assessments to the next level.
Streamline your testing activities end-to-end
Automate the internal pentest life cycle to boost security posture.
Streamline your testing activities end-to-end
Automate the internal pentest life cycle to boost security posture.
Continuous Security
Continuous Security
Protect your attack surface
Protect your attack surface
In today’s dynamic world, security is no longer about fortifying rigid structures. It’s about keeping watch and securing change.
Carry out a continuous evaluation of your attack surface with techniques and methodologies used by real attackers.
In today’s dynamic world, security is no longer about fortifying rigid structures. It’s about keeping watch and securing change.
Carry out a continuous evaluation of your attack surface with techniques and methodologies used by real attackers.
Talk to our experts
Why Continuous Security?
Why Continuous Security?
● Full visibility, periodically: Not before. Not after. Always keep track of your dynamic attack surface to guarantee constant coverage.
● Eliminate Noise: Full coverage requires using several scanners. Let us pinpoint crucial data from an overwhelming amount of results.
● Actionable results: Results will be handed after triage, and with a recommended action course, through Faraday platform.
● Full visibility, periodically: Not before. Not after. Always keep track of your dynamic attack surface to guarantee constant coverage.● Eliminate Noise: Full coverage requires using several scanners. Let us pinpoint crucial data from an overwhelming amount of results.
● Actionable results: Results will be handed after triage, and with a recommended action course, through Faraday platform.
Faraday Platform
Our Technology allows you to define and execute your own actions from different sources with your own schedule and automatically import outputs into your repository. With +150 integrations, an easy-to-use Faraday-Cli, an RESTful API and a flexible scheme to develop your own Agents, our platform brings a unique alternative to create your own automated and collaborative ecosystem.
Our Technology allows you to define and execute your own actions from different sources with your own schedule and automatically import outputs into your repository. With +85 plugins, an easy-to-use Faraday-Cli, an RPC API and a flexible scheme to develop your own Agents, our platform brings a unique alternative to create your own automated and collaborative ecosystem.
Work Methodology
Work Methodology
After signing in
After signing in
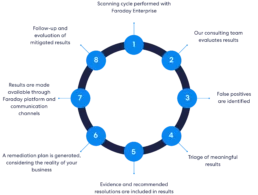
Continuous Security Process
Continuous Security Process
Create resistance,
be one step ahead
Increase vulnerability assessment accuracy, prioritize, and identify optimal remediation options to reduce overall business risk.Our product enables you to reduce the greatest amount of risk with the least amount of effort through:
Vulnerability Management Offensive Security Application Security
Talk to our experts
Create resistance,
be one step ahead
Increase vulnerability assessment accuracy, prioritize, and identify optimal remediation options to reduce overall business risk.
Our product enables you to reduce the greatest amount of risk with the least amount of effort through:
Vulnerability Management
Offensive Security
Application Security
Talk to our experts
Own a complete solution
for vulnerability management
Own a complete solution
for vulnerability management
A security platform with multiple workspaces, users and more that will allow you
to have full visilibility of your attack surface and protect your business.
A security platform with multiple workspaces, users and more that will allow you
to have full visilibility of your attack surface and protect your business.
Corporate Demo
Free Trial
Experience All Corporate Features for a Limited Time
What’s included
Users: Unlimited Workspaces: Unlimited
Assets: Licenced
Reporting: PDF & .docx
Professional
$670/monthly*
*Billed Annually
Loved by both pentesters and security teams. Scan and report easily, all in one place.
What’s included
Users: Licenced (x5) Workspaces: Licenced (x5)
Assets: Licenced (x512)
Reporting: PDF & .docx
Corporate
$1875/monthly*
*Billed Annually