Doggie: A Must-Have Open Source Tool for Car Hacking and Automotive Security

At Faraday, we are passionate about advancing the field of cybersecurity. One of our key areas of focus is Car Hacking Research. Since the early 2000s, vehicles have evolved from purely electro-mechanical machines to complex computer networks on wheels. Modern cars contain over 100 million lines of code—more than some commercial aircraft. As vehicles become increasingly connected and reliant on electronic systems, understanding and securing these systems is more relevant than ever.
To make automotive cybersecurity research more accessible and affordable, we developed Doggie, an open-source and modular CAN Bus – USB adapter. Whether you’re a hobbyist, researcher, or professional, Doggie is designed to simplify working with CAN Bus networks (Controller Area Network), enabling secure exploration and development in the automotive space.
The Importance of CAN Bus in Vehicles
Before delving into Doggie, let’s briefly discuss the Controller Area Network (CAN) Bus, the backbone of modern vehicle communication. CAN Bus can connect critical electronic control units (ECUs) for the engine, brakes, transmission, and even some comfort, information display, and entertainment systems. This network enables seamless communication between these systems, ensuring the vehicle operates efficiently and safely.
For cybersecurity professionals and enthusiasts, CAN Bus represents a critical area for exploration. It offers insights into how vehicles work and the opportunity to secure them against potential threats.
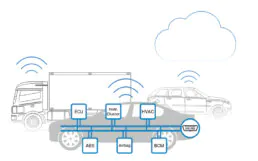
About Doggie
Doggie is a modular, flexible, open-source adapter that bridges the gap between a computer and a CAN Bus network using USB. Built with affordability and adaptability in mind.
Its compatibility with SocketCAN on Linux, Python-can, and other slcan-compatible software ensures seamless integration with existing CAN Bus analysis, sniffing, and injection tools. Doggie also supports ISO-TP, making it perfect for standard and advanced CAN Bus applications. Whether running diagnostics, experimenting with custom in-car functionalities, or performing penetration tests, Doggie provides the tools you need to succeed.
The project emphasizes modularity, allowing users to select from various hardware configurations with different microcontrollers and CAN transceivers. This makes it accessible and cost-effective. Doggie adapts to your needs whether you’re using a microcontroller’s built-in CAN controller or an MCP2515 (SPI to CAN) module.
You can create your own DIY Doggie only by choosing a microcontroller, a CAN interface, and a Serial interface combination. Six possible configurations are available today, and more hardware support is coming!
Microcontrollers:
- Raspberry Pi Pico (RP2040)
- STM32F103C8 (Bluepill)
- ESP32
CAN Controllers:
- Built-in CAN controllers
- MCP2515 (SPI to CAN)
USB/Serial Connectivity:
- Microcontroller USB (native USB support)
- UART with USB Bridge
Doggie’s modular nature and the fact that it was written purely in Rust with hardware abstraction by design make developing new hardware support easy and fast. Thus, if the hardware you already own or prefer is not supported yet, consider adding support for them. It should take a short time and little effort.
Practical Application: Using Doggie in Real-World Scenarios
Doggie isn’t just a tool for research. It’s a versatile companion for real-world automotive applications. Here are some practical scenarios where Doggie can shine:
1. Vehicle Diagnostics
Accessing real-time diagnostic information, including engine parameters, sensor readings, and fault codes. Doggie enables you to interact with the vehicle like a professional-grade diagnostic tool.
2. Customization
Adding new functionalities to your vehicle by sending custom CAN messages. From controlling actuators to integrating new sensors, the possibilities are endless.
3. Security Assessments
Leveraging Doggie to perform penetration testing and vulnerability analysis on vehicle networks. Identify weak points and explore ways to secure critical systems.
Future Work
At Faraday, we are committed to expanding Doggie’s capabilities to meet the growing needs of the automotive security research community. Looking ahead, our plans include:
1. Broader Hardware Support
Doggie’s modularity is one of its defining strengths, and we aim to make it even more versatile. We are working on extending support to additional microcontrollers, ensuring that users can leverage various platforms for their projects.
2. Wireless Capabilities
We plan to incorporate wireless communication features to enhance Doggie’s flexibility and ease of use. By leveraging the Bluetooth and Wi-Fi capabilities of microcontrollers like the ESP32, Doggie will enable researchers to interact wirelessly with CAN Bus networks, opening up new possibilities for remote diagnostics, testing, and experimentation.
3. A Dedicated CAN Bus Hacking Edition
We are also developing a new version of Doggie specifically tailored to the needs of automotive security researchers. This edition will include built-in features to facilitate various CAN Bus attacks, providing researchers with a powerful toolset for studying and exploiting vulnerabilities.
These enhancements will continue to make Doggie an essential tool for anyone looking to explore, understand, and secure CAN Bus systems. We’re excited about the possibilities and can’t wait to share these new developments with the community.
Conclusion
Doggie represents Faraday’s commitment to empowering the community with tools that democratize automotive cybersecurity research. Whether you’re a seasoned professional or a newcomer to car hacking, Doggie provides a low-cost, versatile solution to explore CAN Bus networks and beyond.
Get Involved
Doggie represents Faraday’s commitment to empowering the community with tools that democratize automotive cybersecurity research. Whether you’re a seasoned professional or a newcomer to car hacking, Doggie provides a low-cost, versatile solution to explore CAN Bus networks and beyond.
Check out the project on GitHub!
Trainings, red teaming services, or continuous scanning? We’ve got you covered. 🚀⚡
Related Posts
August 28, 2025
COD4MW Cheat: A Reverse Engineering Adventure
If you enjoy playing online games, you’ve probably heard about cheaters. People tend to have a negative perception of them, and they’re…
June 17, 2025
¿Tu empresa esta preparada para la nueva ley de ciberseguridad de Chile?
Desde este año entró en vigencia una ley modelo de ciberseguridad en Chile. La tomamos como referencia para desarrollar medidas clave que…


