Faraday v4
Our new version
Our new version
Our new version
from Outer Space
from Outer Space
We make attack surface reduction and risk mitigation possible, simple and accessible to one and all.
Allowing companies to innovate in a secure way, even if there is no security team.
We make attack surface reduction
and risk mitigation possible, simple
and accessible to one and all.Allowing companies to innovate
in a secure way, even if there is
no security team.
Faraday provides subscriptions to suit different types of users
Community
Open source
Faraday is proud of its commitment to Open Source. Join our github to check our latest commits.
What’s included
Users: 1 Workspaces: Unlimited
Assets: Unlimited
Reporting
Professional
$670/monthly*
*Billed Annually
Loved by both pentesters and security teams. Scan and report easily, all in one place.
What’s included
Users: Licenced (x5) Workspaces: Licenced (x5)
Assets: Licenced (x512)
Reporting: PDF & .docx
Corporate
$1875/monthly*
*Billed Annually
Take vulnerability management one step further. Scan, prioritize, report, send tickets and more.
What’s included
Users: Unlimited Workspaces: Unlimited
Assets: Licenced
Reporting: PDF & .docx
For developers
Community
Open source
Install now
Faraday is proud of its commitment to Open Source. Join our github to check our latest commits.
What’s included
Users: 1 Workspaces: Unlimited
Assets: Unlimited
Reporting
For startups
Professional
$670/monthly*
*Billed Annually
Loved by both pentesters and security teams. Scan and report easily, all in one place.
What’s included
Users: Licenced (x5) Workspaces: Licenced (x5)
Assets: Licenced (x512)
Reporting: PDF & .docx
For big companies
Corporate
$1875/monthly*
*Billed Annually
Take vulnerability management one step further. Scan, prioritize, report, send tickets and more.
What’s included
Users: Unlimited Workspaces: Unlimited
Assets: Licenced
Reporting: PDF & .docx
Completely new UI, a smarter organization with Custom Filters.
Our biggest leap in performance and simplicity.
Security for everyone, not just security experts.
Increase your security
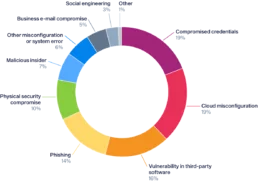
According to the recently IBM's Data Breach 2020 report, more than 41% of data breaches started by targeting misconfigurations and 3rd-party software vulnerabilities.
According to the recently IBM's Data Breach 2020 report, more than 41% of data breaches started by targeting misconfigurations and 3rd-party software vulnerabilities.
Increase your security
According to the recently IBM's Data Breach 2020 report, more than 41% of data breaches started by targeting misconfigurations and 3rd-party software vulnerabilities.

Give us a list of your IPs or URLs, we’ll take it from there
Scan your website and get to work instantly
Part of our enhanced setup process: create your project, invite your colleagues, automatically scan your assets and get to work as soon as possible.
Part of our enhanced setup process:create your project, invite your colleagues, automatically scan your assets and get to work as soon as possible.
Give us a list of your IPs or URLs, we’ll take it from there
Scan your website and get to work instantly
Part of our enhanced setup process: create your project, invite your colleagues, automatically scan your assets and get to work as soon as possible.
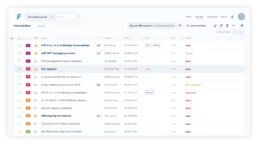
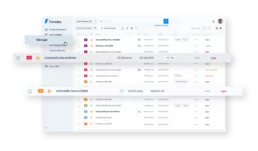
A clear view on the target ensures the arrow won’t miss
Stay updated on where the real risks are
Get both a quick glimpse and a detailed overview of your Assets: identify which have the most risk and therefore need faster action, see all vulnerabilities in them without changing views, assign them to specific Groups (soon!).
Get both a quick glimpse and a detailed overview of your Assets: identify which have the most risk and therefore need faster action, see all vulnerabilities in them without changing views, assign them to specific Groups (soon!).
A clear view on the target ensures the arrow won’t miss
Stay updated on where the real risks are
Get both a quick glimpse and a detailed overview of your Assets: identify which have the most risk and therefore need faster action, see all vulnerabilities in them without changing views, assign them to specific Groups (soon!).
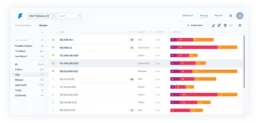
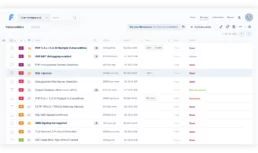
Less clutter = more headspace
Flow seamlessly through our improved interface
Speed up your Vulnerability Management team: updated Vulnerability creation method, right click to make mass changes to your findings, create custom Filters to have all your information neatly organized.
Speed up your Vulnerability Management team: updated Vulnerability creation method, right click to make mass changes to your findings, create custom Filters to have all your information neatly organized.
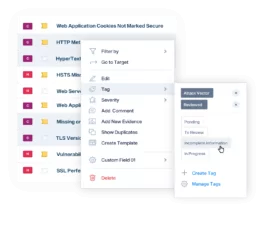
Less clutter = more headspace
Flow seamlessly through our improved interface
Speed up your Vulnerability Management team: updated Vulnerability creation method, right click to make mass changes to your findings, create custom Filters to have all your information neatly organized.
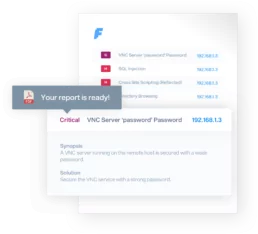
Don’t let all your hard work go unnoticed
Revamped reporting capabilities
From your instance to your client ASAP: generate a Report with all relevant information in PDF, see exactly what’s included in it before it’s created, keep a version control of all changes made to your Reports as you work.
From your instance to your client ASAP: generate a Report with all relevant information in PDF, see exactly what’s included in it before it’s created, keep a version control of all changes made to your Reports as you work.
Don’t let all your hard work go unnoticed
Revamped reporting capabilities
From your instance to your client ASAP: generate a Report with all relevant information in PDF, see exactly what’s included in it before it’s created, keep a version control of all changes made to your Reports as you work.