Released: Open Source Penetration Testing and VM Platform

Faraday was built from within the security community to make vulnerability management easier and enhance our work.
Offensive security had two difficult tasks: designing smart ways of getting new information, and keeping track of findings to improve further work.
This new update brings: New manage, reporting and UI experience
Focus on pentesting
Get your work organized and focus on what you do best. With Faraday community , you may focus on pentesting while we help you with the rest..
Check out the documentation here.
Installation
The easiest way to get faraday up and running is using our docker-compose
Manage your findings
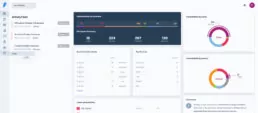
Manage, classify and triage your results through Faraday’s dashboard, designed with and for pentesters.
Get an overview of your vulnerabilities and ease your work.
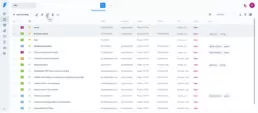
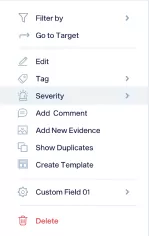
By right clicking on any vulnerability, you may filter, tag and classify your results with ease. You may also add comments to vulnerabilities and add evidence with just a few clicks
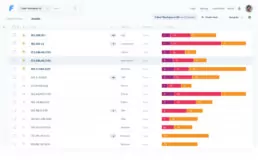
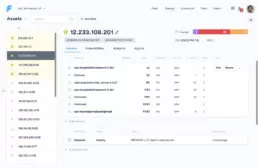
In the asset tab, information on each asset is presented, for a detailed follow-up on every device in your network. This insight might be especially useful if you hold critical data on certain assets, so the impact of vulnerabilities may be assessed through this information. If responsibilities over each asset are clear, this view helps to organize and follow the work of asset owners too.
Here, you can obtain information about the OS, services, ports and vulnerabilities associated with each of your assets, which will give you a better understanding of your scope and help you gain an overview of what you are assessing.
Use your favorite tools
Integrate scanners with Faraday Agents Dispatcher. This feature will allow you to orchestrate the most commonly used security tools and have everything available from your Faraday instance. Once your scan is finished, you will be able to see all the results in the main dashboard.
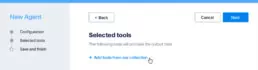
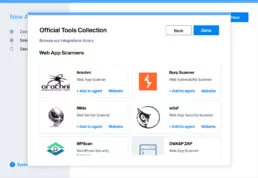
Choose the scanners that best fit your needs.
Deliver executive summaries
Once you’re done, export your results in a CSV format. And quickly generate penetration test reports.
Check out some of our features
Full centralization
With Faraday, you may oversee your cybersecurity efforts, prioritize actions and manage your resources from a single platform.
Elegant integration of scanning tools
Make sense of today’s overwhelming number of tools. Faraday’s technology aligns +150 integrations with your current needs, normalizing and deduplicating vulnerabilities.
Powerful Automation
Save time by automating pivotal steps of Vulnerability Management. Scan, create reports, and schedule pipelines of custom actions, all following your requirements.
Intuitive dashboard
Faraday’s intuitive dashboard guides teams through vulnerability management with ease. Scan, analyze, automate, tag, and prioritize, each with just a few clicks.
Smart visibility
Get full visibility of your security posture in real-time. Advanced filters, navigation, and analytics help you strategize and focus your work.
Easier teamwork
Coordinate efforts by sending tickets to Jira, Gitlab, and ServiceNow directly from Faraday.
Planning ahead
Manage your security team with Faraday planner. Keep up by communicating with your peers and receiving notifications.
Work as usual, but better
Get your work organized on the run when pentesting with Faraday CLI.
Proudly Open Source
We believe in the power of teams, most of our integrations and core technologies are open source, allowing any team to build custom implementations and integrations.
For more information check out our web. www.faradaysec.com
Related Posts
September 11, 2025
Content-Security Policy (CSP) y cómo (no) confiar ciegamente en ella
El Content-Security Policy (CSP) es una de las defensas más efectivas contra vulnerabilidades del tipo Cross-Site Scripting (XSS) y ataques…
August 28, 2025
COD4MW Cheat: A Reverse Engineering Adventure
If you enjoy playing online games, you’ve probably heard about cheaters. People tend to have a negative perception of them, and they’re…


