Cybersecurity is a secondary objective
A programmer is close to a deadline and must work fast. For this one time, they choose to skip certain security protocols. They promise not to do so again but fail to accomplish it.
A rapidly growing business must choose where to locate its budget. They may continue developing their best product, perform a stronger marketing campaign to continue growing, or reduce the probability of data breaches. One of them is the least likely option.
If people know security is extremely important, why do these situations still happen?
Well, maybe it’s because we, as security practitioners, haven’t yet realized security is not that important. What do we mean by this?

Security is nothing but a means to an end.
Security is important; we can all agree on that. But why is it important? Security is nothing but a means to an end.
If there is no business, no security is needed.
For a business, security is as important as it is to that business. Nothing more, nothing less.
Security is as good as the money it saves. As trivial as this may seem, the thought holds valuable insight:
Benefit of a security strategy = P(exploit) * Cost(exploit) — Cost(security strategy)
For a business, the benefit of a security strategy depends not only on how much it reduces the expected cost of data breaches but also on the cost of the security strategy itself.

If we treat security as the top priority, it will be ugly and uncomfortable.
If security is the most important thing in the world, there is no option: programmers, accountants, designers, and managers will have to adapt to our protocols, processes, and requisites.
With no alternative, there would be no incentive to make security more comfortable or to think about broader aspects than reducing risks, such as the economic aspects of security or the effects of different strategies on productivity.
It’s easy to fall into the specialist trap, which is to believe people don’t give that much thought to security because they don’t yet understand its importance, and that the solution is to hold yet another training to go over the exact same points the year before.
The truth is that security is uncomfortable and complicated.
If we offer security solutions without taking into account the fact that security is not that important, we won’t thrive towards better security alternatives.
Treating security as a secondary objective means thinking about its cost as deeply as about its benefits and knowing that security’s cost includes how much time and attention it requires and how much it hinders other activities.
When security is developed this way, the adoption of security measures tends to be more robust. It isn’t seen as an abstract duty but as a naturally good investment. When security is designed as a secondary objective, it is always a good choice because it acknowledges the needs of the business and works precisely to be the best possible investment.
Understanding the role of security is the way to go.
Some factors should be considered to make security more robust, better for businesses, and more easily adopted.
- Simplicity: Recognize time, attention, and human resources as part of the security cost, not only for the security department but for the whole business. This is not easily quantifiable but is real nonetheless: thinking about security is costly. The simpler, the better.
- Adaptability: The more employees go out of their way to meet security needs, the more costly a security strategy is, as it hinders companies’ activities in other areas. The better security adapts to existing workflows, the better it is.
- Efficiency: The main objective of security is not impenetrability but to be a wise investment, which is to enhance the relationship between security cost and security benefit.
Less is more
A good example of these ideas may be seen in the overwhelming number of security tools, scanners, and protocols available. That happens when the design of solutions considers security as the only objective: more and more tools are developed to solve ever more specific issues, with no focus on how businesses will integrate the use of tools in the market.
The bottleneck in security is no longer on the existence of solutions to different issues but rather on integrating available solutions into the most efficient strategy overall.
At Faraday, we addressed the problem by focusing on a crucial and time-intensive process, vulnerability management, and developed a platform to make it simple, adaptable, and efficient.
Our objective was to focus on heuristic design techniques to make the platform simple and easy to learn while allowing teams to carry out all vulnerability management processes from a single platform, improving comfort, efficiency, and speed.
The first steps included several technical challenges:
- integrating plugins for scanning tools available,
- easing the triage process,
- developing continuous visualization techniques,
- allowing teams to create reports within the platform.
But even while addressing them, we never lost focus on the search for comfort, ease of use, and integrity, the feeling that the platform works as an integrated whole.
Later, and building over that, we improved efficiency and reach, by
- Allowing for automation of key steps, such as scanning or triaging of vulnerabilities,
- Integrating ticketing platforms such as Jira, Gitlab, or ServiceNow to allow teams to follow a vulnerability’s lifecycle through to its mitigation.
The result was the Faraday Platform.
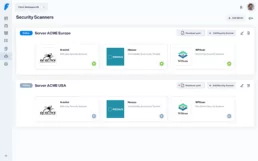
Apart from being simple and efficient, Faraday is adaptable because security teams of any size or maturity may use it however they need, but also because it’s so easy to deploy a battery of scanners according to the product they develop.
Treating security as a secondary objective is, perhaps, the main strength of Faraday.
The main point is not that it improves security but that it does so by easing people’s jobs.
Are you interested in our products? Get in touch with us. ⚡🚀
Related Posts
September 22, 2025
Lanzamiento Faraday v5.16
¡Bienvenido a la nueva versión de nuestra plataforma de Gestión de Vulnerabilidades! Esta actualización introduce filtros granulares por…
September 22, 2025
Faraday v5.16
Welcome to Faraday v5.16, the new version of our Vulnerability Management platform! This update introduces granular filters by date and…

