Getting started: centralize your vulnerability data
How to import vulnerabilities
How to get started / Getting started #2: Centralize your vulnerability data
Introduction
Faraday makes security easier by allowing you to centralize vulnerability data. In it’s dashboard, you’ll be able to:
Visualize security information in preferred ways, Carry out vulnerability management, Build reports on selected data, Automate scanning and classification tasks, and Integrate security fixes to your favorite ticketing platform.
To get started, you’ll need to get your vulnerabilities into your workspace. This may be done by performing a security scan within the platform, or by importing the vulnerabilities you want to work with.
Where to import vulnerabilities:
After signing up and being able to perform a First Scan of your attack surface, you’ll have the option to upload new vulnerabilities.
After this first step, vulnerabilities may be downloaded and uploaded through the Manage section of your vulnerabilities portal.
1. Uploading vulnerabilities
In the Manage Vulnerabilities section, you’ll be able to import vulnerabilities through the Add Vulnerability button, on top of your dashboard.
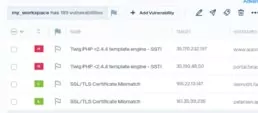
The button will display a menu, in which you’ll find the option to import vulnerabilities from a file. By selecting on it, a window will open, where vulnerability files may be uploaded.
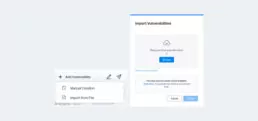
If uploaded files were downloaded from other Faraday workspaces, no formatting issues will arise. Files uploaded from other sources should be CSV files in which:
Each row represents a vulnerability. Each row represents an attribute. Column names should be the ones in this template to be recognized. To learn more about vulnerability attributes and headers, as well as how to include custom attributes, see this tutorial.
2. Dowloading vulnerabilities
In the manage vulnerabilities section, you’ll find the option to download data from a workspace on the top right corner of your dashboard.