A single platform for agile vulnerability management
A single platform for agile vulnerability management
How to get started / A single platform for agile vulnerability management
There are only two ways of finding a vulnerability. Either you do, or somebody else does. Cybersecurity is all about being one step ahead
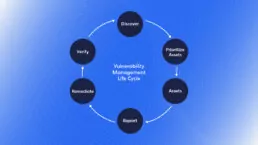
Faraday allows you to optimize the vulnerability management process, making it more accessible, agile, scalable and efficient. The platform’s design eases the classification, prioritization, and handling of vulnerabilities, while allowing users to boost their efficiency by automating key steps of the process. Let’s see how this works. The vulnerability management process consists of six steps. Faraday’s technology optimizes and smoothens the process as a whole, allowing you to manage it from a single platform.