Intuitive dashboard for agile vulnerability management
Intuitive dashboard for agile vulnerability management
How to get started / Intuitive dashboard for agile vulnerability management
The core of Faraday platform is its dashboard. Here’s where most decisions are made.
The full power of the dashboard is in vulnerability management, as shown in our introduction to Faraday. If you haven’t yet, it might be helpful to follow these instructions after creating an account and scanning your domain or uploading your vulnerabilities to Faraday.
In Faraday’s navigation bar you’ll find three sections: the activity feed, the vulnerability dashboard and the asset dashboard, each designed to guide you through the key steps of vulnerability management.
Activity Feed

In your activity Feed, you’ll find an overview of your vulnerabilities and attack surface. Created to ease the identification of general traits and patterns of your security risks, this tab will help you get insight for the design of smart and efficient security strategies.
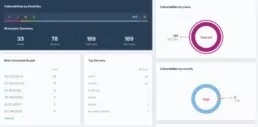
In your activity feed, you’ll also find your latest vulnerabilities and the latest updates to vulnerabilities, to get full transparency, visibility and communication through the vulnerability management process.
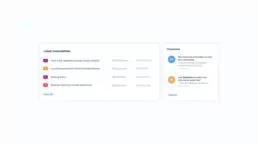
Assets
In the asset tab, information on each asset is presented, for a detailed follow-up on every device in your network. This insight might be especially useful if you hold critical data on certain assets, so the impact of vulnerabilities may be assessed through this information. If responsibilities over each asset are clear, this view helps to organize and follow the work of asset owners too.
It will show you the type and number of vulnerabilities associated with each of your assets, as well as their severity, next to the asset ip and hostname.
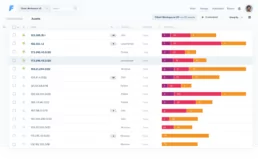
Any asset may be clicked to display the full list of its vulnerabilities, have a view of which services are open in said asset, and to get general information on the asset’s history.
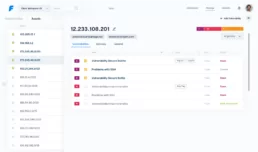
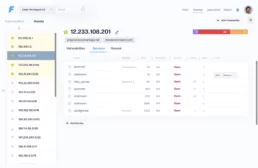
Vulnerabilities
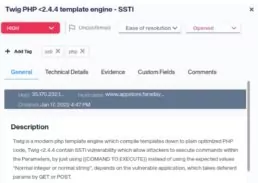
On the manage vulnerabilities tab, information is organized by vulnerabilities. Here is where most vulnerability management happens. Vulnerabilities may be prioritized, assigned, tagged and updated.
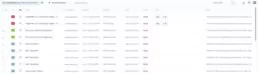
By right clicking on any vulnerability, a menu will be displayed:
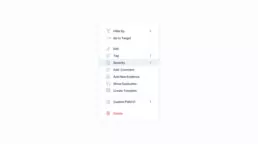
It will allow you to tag and edit vulnerabilities, access the vulnerability’s link as well as the API call link, and easily update its status and severity.
You will be able to add comments to the vulnerability, in which you may tag other users and they will receive a notification, and to update evidence of the vulnerability, all with just a few clicks.
If the volume of vulnerabilities is too high, you may want to filter what to see to ease your navigation. To choose which information you wish to be shown, the filter and column features may be accessed on the top-right corner.
By filtering, you may specify vulnerabilities by traits, and tags, in order to work on specific groups.

On the columns menu, you may choose which attributes of the vulnerabilities you wish to be shown on your dashboard.
By clicking on each of the vulnerabilities, you’ll be able to access all their information. Read the description to get to know it in detail and the recommended resolution on how to solve it. For any convenient modification, every field may be edited by clicking on it.